How to Remove Trojan:Win32/Patched.AO (Uninstall Guide)
TrojansIt makes sense that, as security threats are increasing, no matter whether we are a large corporation, a small business or a home computer user, that all of us need to know as much as we can about how to protect our PCs and data from the myriad of different types of malware that have been created with the express intention of doing us harm. In that sense, one piece of malicious software that you really should take steps to educate yourself upon is something known as Trojan:Win32/Patched.AO. This very unpleasant type of malware is definitely something that you need to stay one step ahead of so why not read on as I tell you some easy to implement tactics that will help you stay safe in the face of a Trojan. And if your computer is already infected, you can skip to the removal guide below.
First of all, just what is Trojan:Win32/Patched.AO malware?
In short, it's a Trojan horse. Trojan Horses are one of the most distinctively named types of malicious software and it is probably quite likely that you have already heard of them. They are also commonly used by cyber criminals and considering that they are one of the nastiest malwares on the block you should really take steps to protect yourself.
Trojan:Win32/Patched.AO can cause untold havoc on your computer by corrupting or deleting your files and documents and it can also have a horrible knock on affect on your PC's security posture too and therefore leave you wide open to further attacks. Some variants of Trojan:Win32/Patched.AO Trojan can even watch which websites you visit and what keys you type so that they can track your online usage and then steal your login details, passwords or bank account details. We are talking about pretty hardcore stuff here! Most of the time, it's packed with LaSuperba and other adware. So, not only you will get strange DNSAPI.dll is missing error messages but also pop-up adverts on your computer. What is more, it can hijack DNS settings so that you won't be able to access certain websites or even open your web browser. The bad news is that this Trojan horse is new and not all malware removal tools can detect and properly remove it from the system. Let's take MSE for example. Yes, it detects Trojan:Win32/Patched.AO but sometimes fails to remove it. I'm not exactly sure why but my guess would be that it can't access files blocked by group policy. And that's exactly what this Trojan does, it modifies group policies. By the way, Windows registry as well. Needless to say, it might be difficult to remove this malware from your computer.
How the Trojan Horse got its name
If you are wondering why a Trojan Horse is so called all you need to do is to think back to your school history lessons and the myths of ancient Greece. Remember the tale about the giant wooden horse which the Greek built to defeat their sworn enemies, the Trojans? In this ancient story, the Greek army constructed a massive hollow horse and concealed some of their soldiers inside its stomach. They then offered it to the Trojan people as a peace offering, ostensibly to bring this checkmate of a war to its conclusion. Alas, the people of Troy didn't realize that their gift was a cunning tactic that enabled the Greeks to infiltrate their city from the inside by waiting until night fell and sneaking out of the horse and opening the gates to their fellow soldiers. And that is exactly how Trojan Horse malware got its name.
You see, today's Trojan Horses use exactly the same MO: they are designed to look innocent - or useful – making you think that it is perfectly safe to download and install them. The problem is, they are just as cunning as the ancient Greeks were and that fun game, latest music download or lifestyle application could actually be a Trojan:Win32/Patched.AO.
Protect your computer!
Trojan:Win32/Patched.AO is usually sent by email or instant messengers so refrain from opening attachments or clicking on links if you don't 100% trust the sender.
How do I remove Trojan:Win32/Patched.AO?
If your computer is already infected and you can't seem to get rid of this high risk Trojan horse, please follow the steps in the removal guide below. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
1. Firs of all, run the SFC /SCANNOW command to fix corrupted system files before running anti-malware software. If you don't know how to do that, please watch system file check for Windows 7 or system file check for Windows 8/10 video depending on your version of Windows.
2. Then, download anti-malware software and run a full system scan. It will detect and remove this Trojan horse from your computer. You may then follow the manual removal instructions below to remove the leftover traces of this malware. Hopefully you won't have to do that.
3. And finally, download and run TDSSKiller. Press the button Start scan for the utility to start scanning.
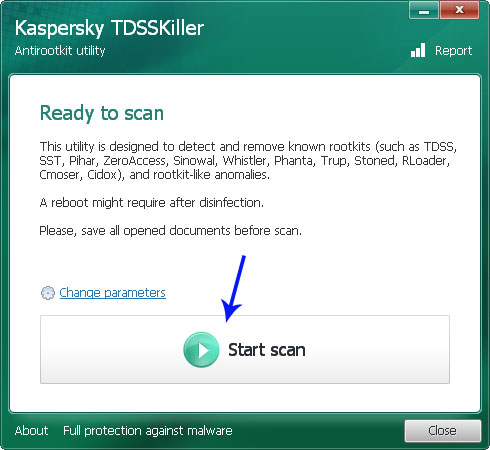
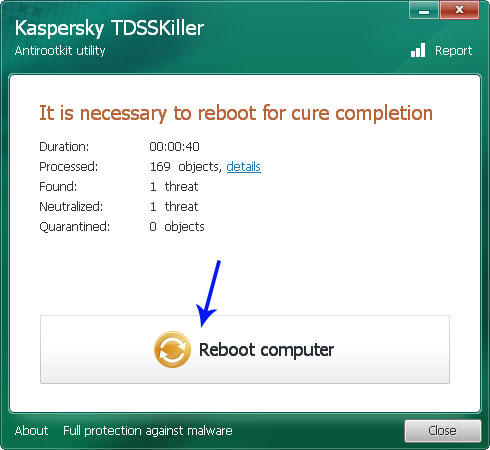
4. Wait for the scan and disinfection process to be over. Then click Continue. Please reboot your computer after the disinfection is over.
First of all, just what is Trojan:Win32/Patched.AO malware?
In short, it's a Trojan horse. Trojan Horses are one of the most distinctively named types of malicious software and it is probably quite likely that you have already heard of them. They are also commonly used by cyber criminals and considering that they are one of the nastiest malwares on the block you should really take steps to protect yourself.
Trojan:Win32/Patched.AO can cause untold havoc on your computer by corrupting or deleting your files and documents and it can also have a horrible knock on affect on your PC's security posture too and therefore leave you wide open to further attacks. Some variants of Trojan:Win32/Patched.AO Trojan can even watch which websites you visit and what keys you type so that they can track your online usage and then steal your login details, passwords or bank account details. We are talking about pretty hardcore stuff here! Most of the time, it's packed with LaSuperba and other adware. So, not only you will get strange DNSAPI.dll is missing error messages but also pop-up adverts on your computer. What is more, it can hijack DNS settings so that you won't be able to access certain websites or even open your web browser. The bad news is that this Trojan horse is new and not all malware removal tools can detect and properly remove it from the system. Let's take MSE for example. Yes, it detects Trojan:Win32/Patched.AO but sometimes fails to remove it. I'm not exactly sure why but my guess would be that it can't access files blocked by group policy. And that's exactly what this Trojan does, it modifies group policies. By the way, Windows registry as well. Needless to say, it might be difficult to remove this malware from your computer.
How the Trojan Horse got its name
If you are wondering why a Trojan Horse is so called all you need to do is to think back to your school history lessons and the myths of ancient Greece. Remember the tale about the giant wooden horse which the Greek built to defeat their sworn enemies, the Trojans? In this ancient story, the Greek army constructed a massive hollow horse and concealed some of their soldiers inside its stomach. They then offered it to the Trojan people as a peace offering, ostensibly to bring this checkmate of a war to its conclusion. Alas, the people of Troy didn't realize that their gift was a cunning tactic that enabled the Greeks to infiltrate their city from the inside by waiting until night fell and sneaking out of the horse and opening the gates to their fellow soldiers. And that is exactly how Trojan Horse malware got its name.
You see, today's Trojan Horses use exactly the same MO: they are designed to look innocent - or useful – making you think that it is perfectly safe to download and install them. The problem is, they are just as cunning as the ancient Greeks were and that fun game, latest music download or lifestyle application could actually be a Trojan:Win32/Patched.AO.
Protect your computer!
Trojan:Win32/Patched.AO is usually sent by email or instant messengers so refrain from opening attachments or clicking on links if you don't 100% trust the sender.
How do I remove Trojan:Win32/Patched.AO?
If your computer is already infected and you can't seem to get rid of this high risk Trojan horse, please follow the steps in the removal guide below. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Trojan:Win32/Patched.AO Removal Guide:
1. Firs of all, run the SFC /SCANNOW command to fix corrupted system files before running anti-malware software. If you don't know how to do that, please watch system file check for Windows 7 or system file check for Windows 8/10 video depending on your version of Windows.
2. Then, download anti-malware software and run a full system scan. It will detect and remove this Trojan horse from your computer. You may then follow the manual removal instructions below to remove the leftover traces of this malware. Hopefully you won't have to do that.
3. And finally, download and run TDSSKiller. Press the button Start scan for the utility to start scanning.

4. Wait for the scan and disinfection process to be over. Then click Continue. Please reboot your computer after the disinfection is over.







