You see, the way these cyber criminals work is by preying on your vulnerability. Imagine the scenario; you’re at home, or possibly even worse in the office surrounded by your colleagues, when suddenly your computer freezes and on your screen appears a message purportedly from the FBI or other police or governmental agency, telling you that you are in serious trouble for violating the law and accessing, downloading or storing illegal content such as X rated pornography of a very distasteful nature or you’ve been visiting terrorist websites. This is police themed ransomware – also known as the ‘Police Trojan’ – a program that has infiltrated your computer’s operating system to display a rogue message claiming that it is from a law enforcement agency.
You will most likely be told that your IP address has been detected engaging in illegal activity and you will be asked to pay a fine, usually $300, using a prepaid card such as MoneyPak, Ukash or PaySafeCard. Malware creators prefer using these methods of payment (rather than PayPal for example) as transactions made via them are difficult to trace and cannot be reversed.
FBI your computer has been locked virus originated back in 2011 and initially targeted PC users in Western Europe, including the UK, France, Spain, Italy, Austria and Belgium, however these days its international boundaries know no limits and the USA and Canada have both seen a massive increase in crimes of this nature. Indeed cyber criminals can make hundreds of thousands of dollars each month with these scams.
Experts investigating cyber-crime have now also found that in addition to more countries being added to the list but that they now target people very specifically in an attempt to convince more people that their fake ‘police’ messages are real. One way of doing this is tailoring the payment methods to the country – for example the UKash card is not known in the States therefore a rogue police notice targeting an inhabitant of the US, for example the one that purports to be from the Computer Crime and Intellectual Property Section of the U.S. Department of Justice will only ask for payment of the fine via the PaySafeCard.
In the United States the victim will normally be asked to pay a not inconsiderable $300 fine via the MoneyPak or PaySafeCard and just to hammer the message home and make payment even easier the thoughtful hackers will include the logos of supermarkets and stores where you can purchase vouchers.
If you’re unlucky enough to be a victim of police themed "FBI your computer has been locked" virus you may well find yourself tempted to click on the ‘pay now’ button. After all, having your PC frozen and a message from the FBI telling you that you are a known visitor of hardcore and illegal adult content sites or a threat to national security is enough to send anyone into a panic. Even if you do suspect that the message may be a computer virus and the work of a hacker, you might be too worried or embarrassed about taking your computer to a store to get it checked out…just in case you did click on something pornographic, either by choice or by accident.
The best thing to do is to follow the removal instructions below to unlock your computer and get rid of the "FBI your computer has been locked" virus. Whatever you do don’t be tempted to pay the fine – as seen, this can be a lot of money and besides, there’s no guarantee that your computer will be returned to normal as many hackers simply take the money and leave you stranded; out of pocket and still with a locked computer.
And of course, as with all malware, having a first rate and up to date antivirus program installed on your computer is the first major step in protecting yourself against online crime. If you have any questions, please leave a comment below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Method 1: System Restore in Safe Mode with Command Prompt:
1. Unplug your network cable and manually turn your computer off. Reboot your computer is "Safe Mode with Command Prompt". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Command Prompt" and press Enter key.
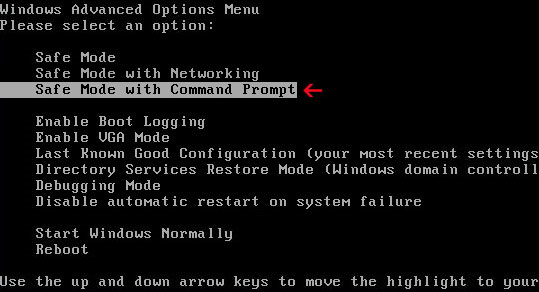
2. Make sure you log in to an account with administrative privileges (login as admin).
3. Once the Command Prompt appears you have few seconds to type in explorer and hit Enter. If you fail to do it within 2-3 seconds, the FBI virus will take over and will not let you type anymore.
4. If you managed to bring up Windows Explorer you can now browse into:
- Win XP: C:\windows\system32\restore\rstrui.exe and press Enter
- Win Vista/Seven: C:\windows\system32\rstrui.exe and press Enter
6. Download recommended anti-malware software (direct download) and run a full system scan to remove the FBI virus.
Method 2: System Restore in Safe Mode:
1. Power off and restart your computer. As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode" and press Enter key.
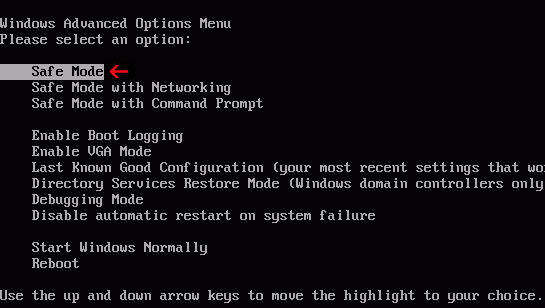
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Once in there, go to Start menu and search for "system restore". Or you can browse into the Windows Restore folder and run System Restore utility from there:
- Win XP: C:\windows\system32\restore\rstrui.exe double-click or press Enter
- Win Vista/7/8: C:\windows\system32\rstrui.exe double-click or press Enter
4. Select a restore point from well before the FBI virus appeared, two weeks should be enough.
5. Restore it. Please note, it can take a long time, so be patient.
6. Once restored, restart your computer and hopefully this time you will be able to login (Start Windows normally).
7. At this point, download recommended anti-malware software (direct download) and run a full system scan to remove the FBI virus.
Method 3: Using MSConfig in Safe Mode:
1. Power off and restart your computer. As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode" and press Enter key.

NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Once in there, go to Start menu and search for "msconfig". Launch the application. If you're using Windows XP, go to Start then select Run.... Type in "msconfig" and click OK.
3. Select Startup tab. Expand Command column and look for a startup entry that launches randomly named file from %AppData% or %Temp% folders using rundll32.exe. See example below:
C:\Windows\System32\rundll32.exe C:\Users\username\appdata\local\temp\regepqzf.dll,H1N1
4. Disable the malicious entry and click OK to save changes.
5. Restart your computer. This time Start Windows normally. Hopefully, you won't be prompted with a fake FBI screen.
6. Finally, download recommended anti-malware software (direct download) and run a full system scan to remove the FBI virus.
Method 4: Manual removal, Safe Mode (requires registry editing) :
1. Unplug your network cable and manually turn your computer off. Reboot your computer in "Safe Mode". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode" and press Enter key.

NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. When Windows loads, open up Windows Registry Editor.
To do so, please go to Start, type "registry" in the search box, right click the Registry Editor and choose Run as Administrator. If you are using Windows XP/2000, go to Start → Run... Type "regedit" and hit enter.
3. In the Registry Editor, click the [+] button to expand the selection. Expand:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
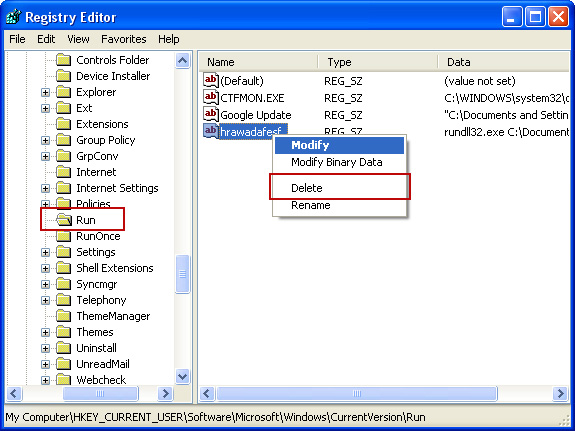
Look on the list to the right for an randomly named item. Write down the file location. Then right click the randomly named item and select Delete. Please note that in your case the file name might be different. Close Registry Editor.
In our case the malicious file (pg_0rt_0p.exe) was located in Application Data folder. So, we went there and simply deleted the file. We're running Windows XP.
File location: C:\Documents and Settings\Michael\Application Data\
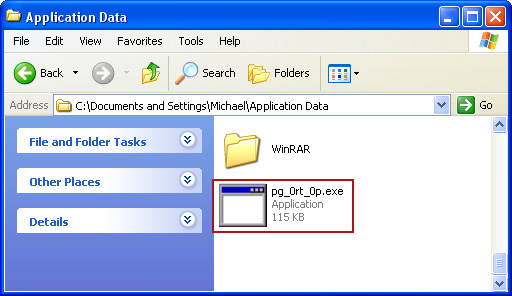
If you are using Windows Vista or Windows Seven, the file will be located in %AppData% folder.
File location: C:\Users\Michael\AppData\Romaming\
Finally, go into Windows Temp folder %Temp% and click Date Modified so the newest files are on top. You should see an exe file, possibly with the name pg_0rt_0p.exe (in our case it was exactly the same), but it may be different in your case. Delete the malicious file.
One more thing, check your Programs Startup list for the following entry:
[UserPATH]\Programs\Startup\ctfmon.lnk - C:\Windows\system32\rundll32.exe pointing to [UserPATH] \Temp\wpbt0.dll,FQ10 (or FQ11)
In our case it was ctfmon.lnk pointing to malicious file which then loads the fake ransom warning. Please note that in your case the file name might be different, not necessarily ctfmon.lnk. Simply disable or remove (if possible) such entry and restart your computer.
4. Restart your computer into "Normal Mode" and scan the system with legitimate anti-malware software.
5. Download recommended anti-malware software (direct download) and run a full system scan to remove the FBI virus.
FBI MoneyPak Ransomware video:
To learn more about ransomware, please read Remove Trojan.Ransomware (Uninstall Guide).
Tell your friends:
How To Get Rid of the "FBI Your computer has been locked" Virus
4/
5
Oleh
soni agus



