There are so many scams, cons, tricks and attacks out there that it can feel like just the simple act of logging onto your computer could trigger a nightmare scenario. And the sad fact is that it actually can. With that in mind, we're going to take a look at one of those malware programs that use scare tactics to get you to hand over your hard earned cash: TeslaCrypt ransomware. Although not quite as widely discussed as some other types of malware, ransomware is a particularly unpleasant program and one that you shouldn't be tempted to ignore, just because it is not as well known. Once you read what it can do, we think you will agree!
Restore_files.bmp content:
What is TeslaCrypt?
It's a crypto-virus that encrypts your files and appends the extension .abc to the file name of the encrypted files. It also drops restore_files.txt ransom note in each folder and the same information in a HTML file and even BMP file. The ransom note says:
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
What happened to your files ?
All of your files were protected by a strong encryption with RSA-2048.
More information about the encryption keys using RSA-2048 can be found here: http://en.wikipedia.org/wiki/RSA_(cryptosystem)
What does this mean ?
This means that the structure and data within your files have been irrevocably changed, you will not be able to work with them, read them or see them,
it is the same thing as losing them forever, but with our help, you can restore them.
How did this happen ?
Especially for you, on our server was generated the secret key pair RSA-2048 - public and private.
All your files were encrypted with the public key, which has been transferred to your computer via the Internet.
Decrypting of your files is only possible with the help of the private key and decrypt program, which is on our secret server.
What do I do ?
Alas, if you do not take the necessary measures for the specified time then the conditions for obtaining the private key will be changed.
If you really value your data, then we suggest you do not waste valuable time searching for other solutions because they do not exist.
You may not have heard of ransomware but have you heard of cryptoviruses or cryprotrojans? These are all names for the same thing – all equally frightening sounding too. And if you're wondering just what it is that TeslaCrypt ransomware can do, the name will probably give it away. It 'kidnaps' the files or data that you have stored on your computer, holds them to ransom – in other words it encrypts them so that you cannot open them - and then tells you that you will need to pay a ransom in order to regain access to your files. Allegedly you will be sent a code to unlock the files once you have made the payment. But here's the truth: many ransomware programmers will happily accept the payment, or ransom, and leave you high and dry without bothering to send you the code.
Ransomware's scare tactics
To increase the chances of you making payment the ransom note that you receive is often designed to look official – and they can be very convincing. The 'kidnapper' knows that you are far more likely to be scared into paying if their notification comes, not from some shadowy third party, but from a law enforcement agency – the FBI or MI5 for example – depending on where your IP address shows you are. However, not all variants of this ransomware use care tactics. Your ransom note can be slightly different but it's still the same TeslaCrypt ransomware. Certain variants adds a few random letter to restore_files.txt file name for example: restore_files_fgrtl.txt but that really doesn't change anything. It's still the same crypto-virus.
The wording will tell you that you are under investigation for downloading pirated software or files, or for visiting an illegal website and if you pay the fine you’ll be off the hook. It's utter nonsense of course and whatever you do, do not pay a penny.
Ways that TeslaCrypt can infect your computer
There are a few ways that ransomware can infect you so you do need to be careful. It can be embedded within the code of a compromised website, it may be disseminated by email or chat apps, or it can come bundled with another program or download. All every day things that we take for granted when we are online. Once installed, it modifies the Internet Explorer Zone Settings stop you from downloading anti-malware software. It sets security settings to high which means you can't download any executable files. Luckily, this can easily fixed by resting security settings. What is more, it terminates Windows Task Manager, Registry Editor and some other Windows tools that are usually very helpful when dealing with malware. For this reason, you may have to restart your computer in safe mode with networking or only safe mode and try to download anti-malware software from there. Or if you know how to remove Windows registry values you can delete these:
In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
{installation ID} = "%Application Data%\svc{random letters}.exe"
In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce
{installation ID} = "%Application Data%\svc{random letters}.exe"
In HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\system
EnabledLinkConnections = 1
How to get my files back?
If you have a recent backup, wipe your hard disk and reinstall your files. If you don't, try Shadow Explorer program or search your computer for previous versions of files. If you are lucky enough you may find files that were not encrypted and renamed to .abc. But before restoring your files, please remove the ransomware and related malware files from your computer. To do so, please follow the steps in the removal guide below. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing TeslaCrypt (restore_files.txt) ransomware and related malware:
Before restoring your files from shadow copies, make sure the TeslaCrypt is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
Important! If you can't download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again. If you don't know how to do that, please watch this video.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by TeslaCrypt (restore_files.txt) virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
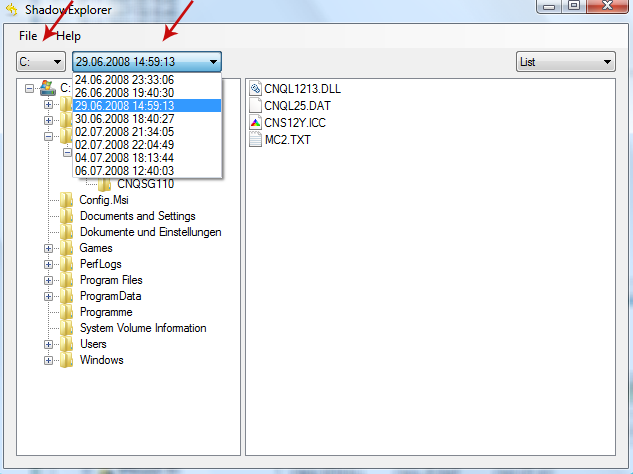
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
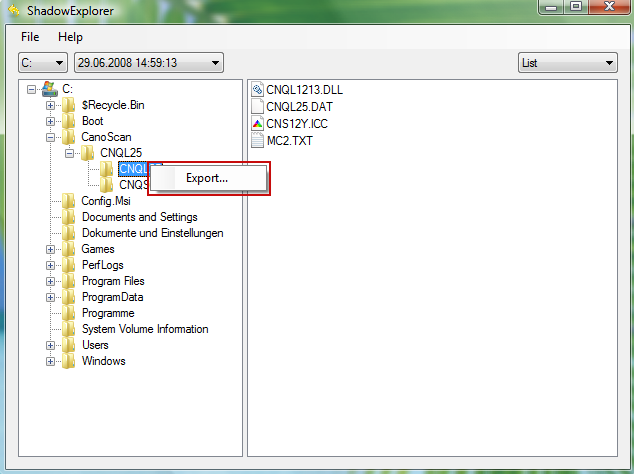
Hopefully, this will help you to restore all encrypted files or at least some of them.
Restore_files.txt and .abc Extension Ransomware Removal Guide
4/
5
Oleh
soni agus


