After all, business is booming in the world of cyber crime and the people that create, distribute and profit from malware and other scams or threats are constantly on top of their game to conjure up even more ways to get us to part with our money.
Understanding ransomware
The problem is, learning about all of the numerous threats out there can feel like information overload and it can be tricky knowing what may affect you. It might not be fun learning about the latest cyber threats but it is most definitely important to take the time to if you want to adequately protect yourself, your data and your bank account.
With that in mind we are now going to take a look at the malware known as MW_ IN FILES ransomware. This is something you certainly should inform yourself about as it is particularly nasty – and that's saying something! Read on and give yourself a fighting chance of defending yourself in the event of a ransomware attack.
What is ransomware?
Put simply, ransomware is a software program that has been created to 'kidnap' the files or data on your PC and hold them hostage by encrypting them until you pay a ransom to get them back. In this case the clue really is in the name. It leaves a ransom with the following information:
Good day. Your computer has been locked by ransomware, your personal files are encrypted and you have unfortunately "lost" all your pictures,
files and documents on the computer. Your important files encryption produced on this computer: videos, photos, documents, etc.
Encryption was produced using unique public key RSA-1024 generated for this computer. To decrypt files you need to obtain the private key.
All encrypted files contain MW_
Your number: [edited]
To obtain the program for this computer, which will decrypt all files, you need to pay
3 bitcoins on our bitcoin address [edited] (today 1 bitcoin was 260 USA dollars). Only we and you know about this bitcoin address.
You can check bitcoin balanse here - https://www.blockchain.info/address/[edited]
After payment send us your number on our mail ttk@ruggedinbox.com and we will send you decryption tool (you need only run it and all files will be decrypted during 1...3 hours)
Before payment you can send us one small file (100..500 kilobytes) and we will decrypt it - it's your garantee that we have decryption tool. And send us your number with attached file
We dont know who are you. All what we need - it's some money.
Don't panic if we don't answer you during 24 hours. It means that we didn't received your letter (for example if you use hotmail.com or outlook.com
it can block letter, SO DON'T USE HOTMAIL.COM AND OUTLOOK.COM. You need register your mail account in www.ruggedinbox.com (it will takes 1..2 minutes) and write us again)
You can use one of that bitcoin exchangers for transfering bitcoin.
In your case the prefix can be different, for example "All encrypted files contain KK_" and email address nown@ruggedinbox.com instead of ttk@ruggedinbox.com. They even change ransom notes probably to make this ransomware campaign more random and avoid unnecessary pattern detection. Anyway, the whole idea remains the same. They encrypt your files, you pay 3 or 4 bitcoins and then email them your unique encryption number.
So I pay the ransom and my files will be returned to me?
This is one of those maddening questions that there is no straight answer to. After all, we are dealing with cyber criminals here and there is absolutely no guarantee that by handing over your credit card details you are going to get your files back. In theory, once you've made the payment, you will be sent a code that enables you to unlock, or decrypt, your inaccessible files but there have been numerous examples of this not being the case and the 'kidnappers' simply taking the money and running, so to speak.
What steps should I take if I've been infected by ransomware?
First and foremost do not hand over any money. As I said, chances are you'll be paying for a big fat nothing. If you have a recent backup, wipe your hard disk and reinstall your files. If you don't, try Shadow Explorer program or search your computer for previous versions of files. If you are lucky enough you may find files that were not encrypted. But before restoring your files, please remove the ransomware and related malware files from your computer. To do so, please follow the steps in the removal guide below. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing Trojan-Ransom.NSIS.ONION.air ransomware and related malware:
Before restoring your files from shadow copies, make sure the Trojan-Ransom.NSIS.ONION.air is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
Important! If you can't download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by Trojan-Ransom.NSIS.ONION.air virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
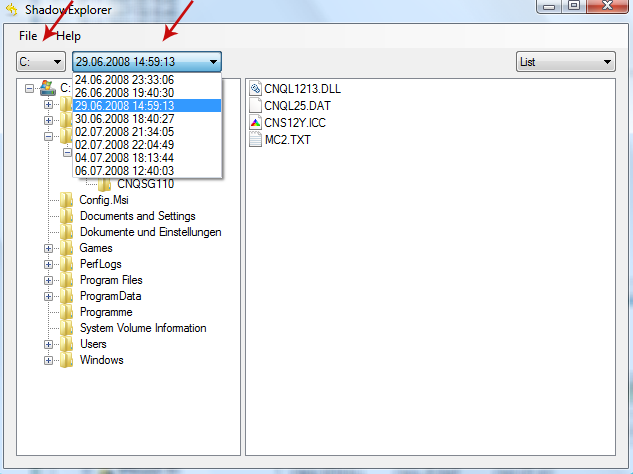
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
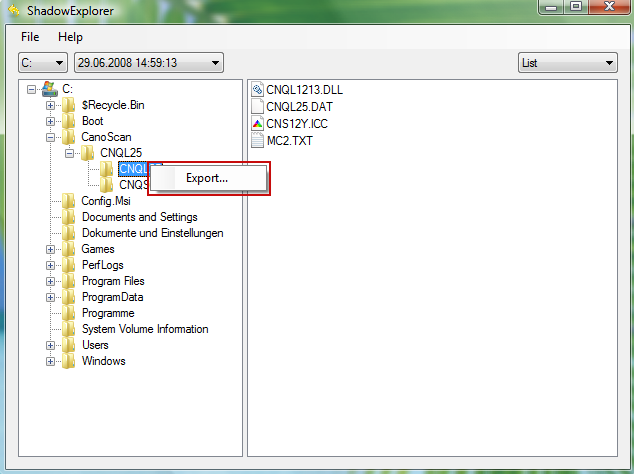
Hopefully, this will help you to restore all encrypted files or at least some of them.
Remove MW_ IN FILES and KK_ IN YOUR DOCUMENTS Ransomware and Restore Encrypted Files
4/
5
Oleh
soni agus


