After all, there is an almost bottomless pit of money to be tapped in to in the cyber crime industry and ransomware programmers are becoming more sophisticated by the day – if not the hour! It's a dizzying thought when you stop to consider the cat and mouse games that producers of anti-virus software and security patches, and malicious software are playing. But what does it mean for people like you on me when all we want to do is connect online to chat to friends, post vacation photos, spend our hard earned cash on a pair of sneakers or – yes, actually do some work!? For a start we know have to be more careful than ever before if we don't want to become yet another statistic in the ongoing online battle between good and evil.
No two types of malicious software are the same which sadly for you and me means there is an endless amount of information to gen up on if we really want to give ourselves the best shot at defending ourselves against the latest threats.
With that in mind, in this article we are going to take a closer look at a type of malicious software program called ransomware. And in particular, the TeslaCrypt variant that changes file extension to .ccc. This malware is not as commonly known as some of the other types of malware – for example spyware or adware but we definitely think it is something that you should learn about how to protect yourself from, considering how unpleasant it is.
What is TeslaCrypt ransomware?
It is a nightmarish program which sounds like it has stepped straight out of the pages of a bad sci-fi movie. Its aim is to get you to pay an amount of money and the way it does this is by causing huge issues on your computer – mainly by making it impossible to use and encrypting your files so that you can't open them. Of course, a good deal of stress and upset are, naturally, part of the package for anyone who thinks that they may not be able to access their documents or photos ever again. And in light of this it can seem like the only option is to pay the sum of money in question.
You have more than likely discerned by now that it is this mode of operating that gives ransomware its name, for it does indeed hold you – or your files - hostage. Once installed, it leaves a ransom note howto_recover_file_* with instructions on how to get your files back. Cyber criminals will probably ask you to pay at least 1 bitcoin for the so called decoder tool.
Should I pay the ransom?
In a word: No! There is NO guarantee that the party responsible will release your files so follow the steps in the removal guide below to remove this ransomware from your computer and hopefully, decrypt your files.
How to get my files back?
If you have a recent backup, wipe your hard disk and reinstall your files. If you don't, try Shadow Explorer and Recuva programs or search your computer for previous versions of files. If you are lucky enough you may find files that were not encrypted and renamed to .ccc. But before restoring your files, please remove the ransomware and related malware files from your computer. To do so, please follow the steps in the removal guide below. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing TeslaCrypt (.ccc extension) ransomware and related malware:
Before restoring your files from shadow copies, make sure the TeslaCrypt is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
Important! If you can't download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again. If you don't know how to do that, please watch this video.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by TeslaCrypt (.ccc extension) virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
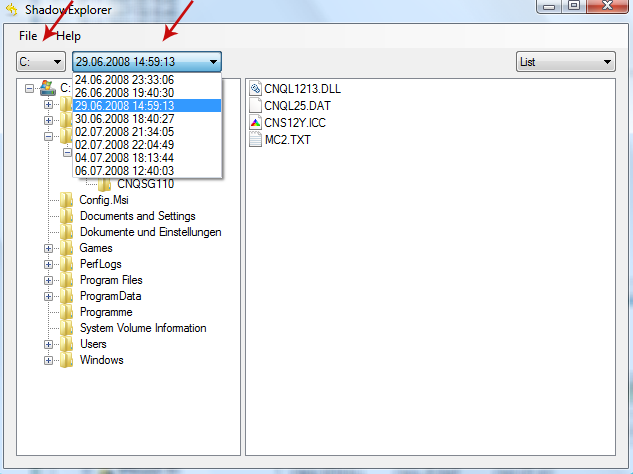
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
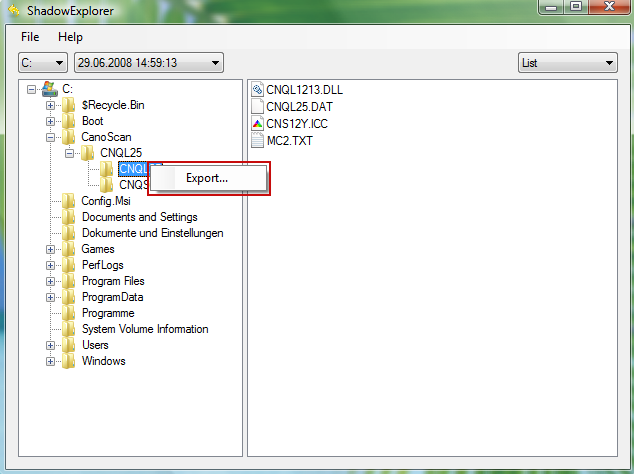
Hopefully, this will help you to restore all encrypted files or at least some of them.
.ccc Extension / howto_recover_file Ransomware Removal Guide
4/
5
Oleh
soni agus



