Remove Inline hook win32k.sys (Uninstall Guide)
RootkitsInline hook win32k.sys is a rootkit that can pose a serious threat to your PC and the data stored on it. If you have it installed on your computer you will certainly know about it as it wastes no time in corrupting your data, writing over your hard drive, rendering files useless or inaccessible and creating instability in your operating system. In order to stay up to date and current with the world of malware, we are going to take a closer look at this rootkit infection. This is a thoroughly unpleasant piece of malware that rubs salt into the wound by appearing to be harmless, convincing you of its innocence, and then in reality, doing you untold damage.
But just how does Inline hook win32k.sys rootkit infect your PC, what does it do once it is up and running, and how can you protect yourself from it?
Like most of us, you probably don't think you put yourself at risk unwittingly and you may even consider yourself somewhat impenetrable or not easily fooled. The passwords that you choose are the right combination of letters and numbers, your top notch anti-virus software is always bang up to date, and you wouldn't dream of opening an email or instant message attachment if you don't know the sender. And that is all very good stuff indeed, however, the sad fact is that rootkits are very, very good at playing on even the most cynical of natures and even worse, they force you into playing a part in their execution too. Such malicious software usually arrives in the form of an unwanted download or as code illegally injected into a legitimate website without the webmaster's knowledge. It can also be received as an email attachment or an instant message from an untrusted source. It can also come packed with Trojan horses, mostly Trojan downloaders.
Inline hook win32k.sys detection indicates that there is a hidden program on your computer with potentially malicious behaviors. Otherwise, why would someone wanted to hide it deep inside your operating system? The answers is pretty obvious, cyber criminals want to gather personal information or even gain a remote access to your computer without your consent. This rootkit installs itself for auto run at Windows startup. It even creates and alternative data steam and injects code into system files. Then it performs some HTTP requests mostly to look up an external IP address and to send PC information as well as receive further commands from control and command server. When such rootkit is installed on your computer you can expect anything to be downloaded and installed onto your PC. It can be spyware, Trojan horses or even adware. Certain variants of Inline hook win32k.sys infection tries to change proxy and DNS servers and redirect all your traffic through web servers controlled by cyber criminals. As a result, they can see what websites you visit and what search queries you make. Such information is very useful and can be used for ad injection and simply sold to third parties.
Inline hook win32k.sys removal can be complicated as you can't simply locate the malicious file and delete it. As a matter of fact, your anti-virus program may not be able to remove it either. To do so, you will have to use a few tools designed to remove rootkits and other deeply embedded malware. If your computer is already infected and you can't seem to get rid of this dangerous rootkit, please follow the steps in the removal guide below. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
1. First of all, download anti-malware software and run a full system scan. It will detect and remove this infection from your computer. You may then follow the manual removal instructions below to remove the leftover traces of this malware. Hopefully you won't have to do that.
NOTE: If you are using Internet Explorer and can't download anti-malware software because "Your current security settings do not allow this file to be downloaded" then please reset IE security settings and try again.
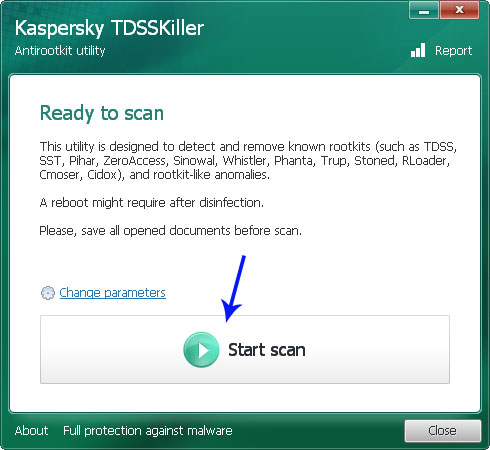
2. Download and run TDSSKiller. Press the button Start scan for the utility to start scanning.
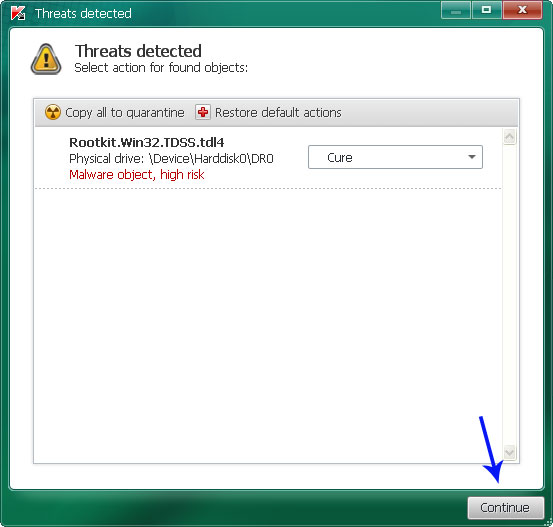
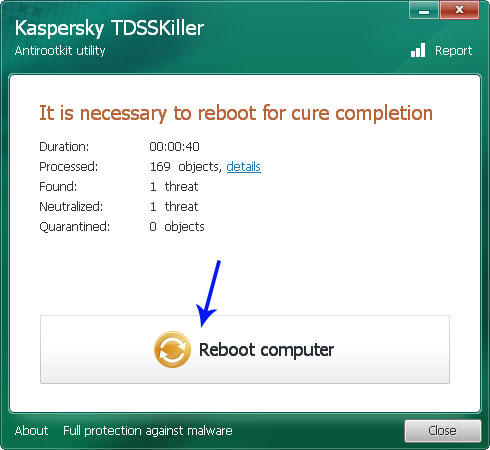
3. Wait for the scan and disinfection process to be over. Then click Continue. Please reboot your computer after the disinfection is over.
But just how does Inline hook win32k.sys rootkit infect your PC, what does it do once it is up and running, and how can you protect yourself from it?
Like most of us, you probably don't think you put yourself at risk unwittingly and you may even consider yourself somewhat impenetrable or not easily fooled. The passwords that you choose are the right combination of letters and numbers, your top notch anti-virus software is always bang up to date, and you wouldn't dream of opening an email or instant message attachment if you don't know the sender. And that is all very good stuff indeed, however, the sad fact is that rootkits are very, very good at playing on even the most cynical of natures and even worse, they force you into playing a part in their execution too. Such malicious software usually arrives in the form of an unwanted download or as code illegally injected into a legitimate website without the webmaster's knowledge. It can also be received as an email attachment or an instant message from an untrusted source. It can also come packed with Trojan horses, mostly Trojan downloaders.
Inline hook win32k.sys detection indicates that there is a hidden program on your computer with potentially malicious behaviors. Otherwise, why would someone wanted to hide it deep inside your operating system? The answers is pretty obvious, cyber criminals want to gather personal information or even gain a remote access to your computer without your consent. This rootkit installs itself for auto run at Windows startup. It even creates and alternative data steam and injects code into system files. Then it performs some HTTP requests mostly to look up an external IP address and to send PC information as well as receive further commands from control and command server. When such rootkit is installed on your computer you can expect anything to be downloaded and installed onto your PC. It can be spyware, Trojan horses or even adware. Certain variants of Inline hook win32k.sys infection tries to change proxy and DNS servers and redirect all your traffic through web servers controlled by cyber criminals. As a result, they can see what websites you visit and what search queries you make. Such information is very useful and can be used for ad injection and simply sold to third parties.
Inline hook win32k.sys removal can be complicated as you can't simply locate the malicious file and delete it. As a matter of fact, your anti-virus program may not be able to remove it either. To do so, you will have to use a few tools designed to remove rootkits and other deeply embedded malware. If your computer is already infected and you can't seem to get rid of this dangerous rootkit, please follow the steps in the removal guide below. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Inline hook win32k.sys Removal Guide:
1. First of all, download anti-malware software and run a full system scan. It will detect and remove this infection from your computer. You may then follow the manual removal instructions below to remove the leftover traces of this malware. Hopefully you won't have to do that.
NOTE: If you are using Internet Explorer and can't download anti-malware software because "Your current security settings do not allow this file to be downloaded" then please reset IE security settings and try again.
2. Download and run TDSSKiller. Press the button Start scan for the utility to start scanning.

3. Wait for the scan and disinfection process to be over. Then click Continue. Please reboot your computer after the disinfection is over.