Usually, Backdoor.Tidserv, Alureon rootkit is able to conceal in the system any processes and files on a disk as well as registry keys described in its configuration. Most of the time it installs own hidden drivers and services as well into the system. For example: H8SRTd.sys or _VOIDd.sys. Such hidden services can be revealed using GMER utility.
You may suspect that your computer is infected with TDSS malware if you encounter at least one of the following symptoms:
- Internet Explorer is hijacked
- Google search result links redirects to totally unrelated or harmful sites that host malicious software or display misleading advertisements, pop-ups and etc.
- You can't access security related websites. This is commonly used method by nearly all widely spread malware in order to protect itself from being removed.
- You can't launch antivirus and antispyware programs. TDSS TDL3 rootkit blocks security software too for an obvious reason. Also note that it may block any other software not only security related.
- Certain Windows system tools are disabled. Task Manager, Registry Editor and others.
TDSS, Alureon, Tidserv, TDL3, TDL4 removal instructions using TDSSKiller utility:
1. Download the file TDSSKiller.exe and execute it. If you can't launch it then rename it to explorer.exe or iexplore.exe. If that fails too, then you will have to change file extension from *.exe to *.com. For example: test123.com.
NOTE: some users make mistakes when changing file extensions. You have to make sure that extension for know file types are not hidden. Otherwise you will get something like test123.com.exe which is the same test123.exe file not test123.com and it won't work. Read how to make extensions of known file types visible below.
a) Double-click on the "My Computer" icon.
b) Select "Tools" from menu and click "Folder Options".
c) Select the "View" tab. Remove the checkmark from the checkbox labeled "Hide file extensions for known file types". Click OK button.
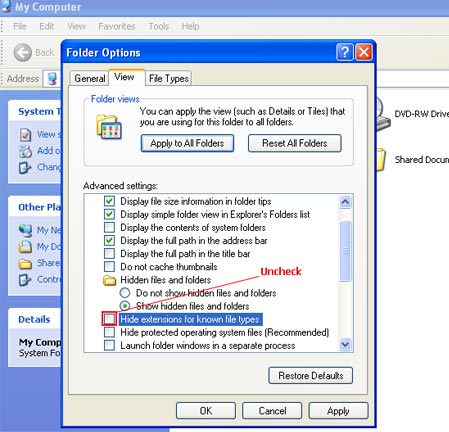
d) Now you can rename TDSSKiller.exe to random.com.
2. Double-click on it to launch TDSSKiller utility. If you receive Windows security warning, please click on the "Run" button to allow TDSSKiller to run.
3. Click the "Start scan" button and wait for the scan be over.
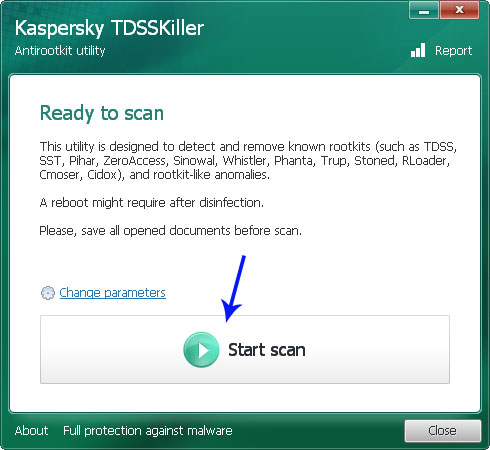
Click Continue.
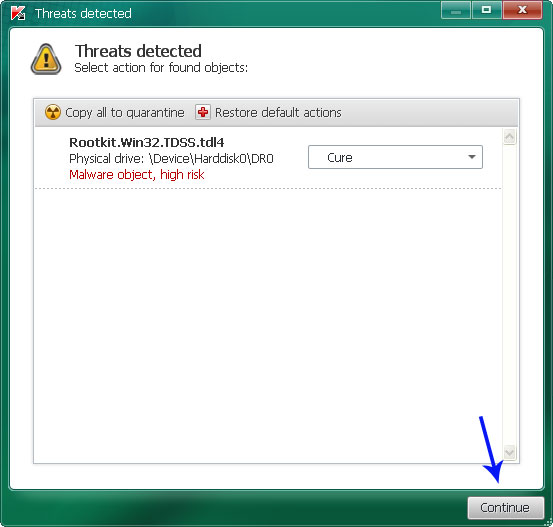
Reboot your computer to remove the rootkit.
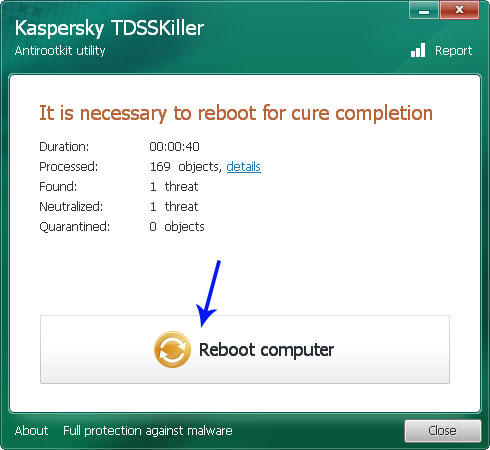
4. Finally, download recommended anti-malware software (direct download) and run a full system scan to remove this rootkit from your computer.
TDSS, Alureon, Tidserv, TDL3, TDL4 files and registry values:
Files:
- C:\WINDOWS\system32\drivers\RDPCDD.sys
- C:\WINDOWS\_VOID[random]\
- C:\WINDOWS\_VOID[random]\_VOIDd.sys
- C:\WINDOWS\system32\drivers\_VOID[random].sys
- C:\WINDOWS\system32\drivers\UAC[random].sys
- C:\WINDOWS\system32\UAC[random].dll
- C:\WINDOWS\system32\uacinit.dll
- C:\WINDOWS\system32\UAC[random].db
- C:\WINDOWS\system32\UAC[random].dat
- C:\WINDOWS\system32\uactmp.db
- C:\WINDOWS\system32\_VOID[random].dll
- C:\WINDOWS\system32\_VOID[random].dat
- C:\WINDOWS\Temp\_VOID[random].tmp
- C:\WINDOWS\Temp\UAC[random].tmp
- %Temp%\UAC[random].tmp
- %Temp%\_VOID[random].tmp
- C:\Documents and Settings\All Users\Application Data\_VOIDmainqt.dll
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\_VOIDd.sys
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\_VOID[random
- HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\UACd.sys
Please share this information with other people:
TDSS, Alureon, Tidserv, TDL3 removal instructions using TDSSKiller utility
4/
5
Oleh
soni agus
