How to Remove Locker Virus and Restore Encrypted Files
RansomwareLocker is a file-encrypting ransom virus (ransomware) that encrypts your files using RSA-2048 encryption algorithm so they are not accessible and repairable without the unique encryption key. I've seen a few different versions of this ransomware so far: Locker v5.52, Locker v3.30, Locker v4.55, Locker v4.81 and Locker v2.60. Basically, it's the same ransomware only with different version numbers. I bet there are even more versions out there but I'm not quite sure why cyber criminals decided to do this. Anyway, no matter which version you have installed on your computer, it's the same ransomware. It does encrypt your files, it's not a joke. If you don't have backups you might be in trouble. This vicious malware is most definitely something that you would be well advised to finding out more about so that you are better able to protect yourself from an attack. It is also extremely useful to know why you shouldn't give in to ransomware's demands and what to do if you have been infected.
Locker virus payment page:
It demands to pay 0.1 BTC and gives information on how to buy Bitcoins. There's also a payment address which is unique for every victim.
What does Locker ransomware do?
You have probably already guessed that the clue to unlocking the way ransomware works is in its name. Locker has been created to kidnap your files or data, freeze them and make them inaccessible or unusable. After doing this the program will send you an updated version of the old fashioned ransom note, demanding that you pay 0.1 BTC (about $25) for your files to be released or unlocked. Once you've paid (which, by the way, you shouldn't – more of that in a minute) you will be sent a code that allows you to unlock your encrypted files. But when we say 'you will be sent' don't take that at face value as many cyber criminals using Locker ransomware will not bother to send you anything, simply taking your money and disappearing, never to be heard of again. And don't think you'll be able to negotiate with them either – these types of people don't tend to have a customer care helpline.
And that's not all...
So that they can ensure you will be more likely to pay, victims of Locker will turn the fear factor up to eleven. You're already wondering if you're ever going to see your files and the data they contain again, but to pile even more stress upon you, many of these so called ransom notes will either tell you that they have been sent by a law enforcement agency, such as the FBI or CIA, or tell you that the unlock code will become invalid and your files destroyed if you don't pay by a certain date. In this case, cyber criminals give you 3 days to pay the ransom. The Locker ransom program says:
All your personal files on this computer are locked and encrypted by Locker [ver]. The encrypting has been done by professional software and your files such as: photos, videos, and cryptocurrency wallets are not damaged but just not readable for now. You can find the complete list with all your encrypted files in the files tab.
The encrypted files can only be unlocked by a unique 2048-bit RSA private key that is safely stored on our server till [date]. If the key is not obtained before that moment it will be destroyed and you will not be able to open your files ever again.
Obtaining your private unique key is easy and can be done clicking on the payment tab and pay a small amount of 0.1 BTC to the wallet address that was created for you. If the payment is confirmed the decryption key will be sent to your computer and the Locker software will automatically start the decrypting process. We have absolutely not interest in keeping your files encrypted forever.
You can still safely use your computer, no new files will be encrypted and no malware will be installed. When the files are encrypted Locker [ver] will automatically uninstall itself.
It's very similar to BitCryptor ransomware. It shows time remaining, lists all the encrypted files and gives you a personal Bitcoint wallet address.
What do I do? Pay the fine and make the problem go away?
It's not a good idea but if you really really care about the files, pay the ransom, although no guarantee that you'll get the files back. Besides, by paying you'll be perpetuating cyber crime. Instead, follow the removal guide below on how to salvage your data and clean your computer ASAP. There are a few tools that can help you to restore at least some of your files without paying a ransom. Even though, there's no guarantee that these tools will help you, there's also no reason not to try them out. Who knows, maybe you will be the lucky one. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
IMPORTANT! Before running anti-malware software and trying to restore your files COPY the encrypted files, your Bitcoin wallet address (see under Payment tab) and %PROGRAMDATA%\rkcl, %PROGRAMDATA%\tor, %PROGRAMDATA%\steg or %PROGRAMDATA%\Digger folder (with files) to external hard drive, CD/DVD or a USB flash key. You should have these in case you decide to pay the ransom or someone creates a decryption tool.
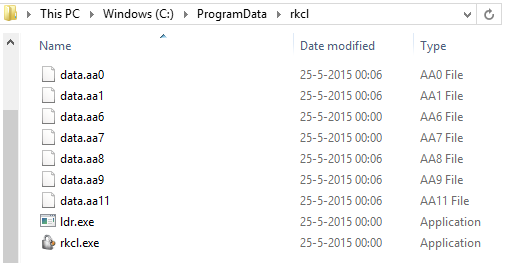
The ransomware is also known to disable certain system features like system restore, delete shadow copies, and prevent the uninstalling of software. This makes it incredibly difficult to remove it or roll back to solve the issue.
Before restoring your files from shadow copies, make sure Locker virus is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
IMPORTANT! If you can't download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again. Also, try to disable bclock.exe using Process Explorer.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Use Locker Unlocker decryption tool. This tool is designed to decrypt files encrypted by the Locker ransom virus.
Method 4: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
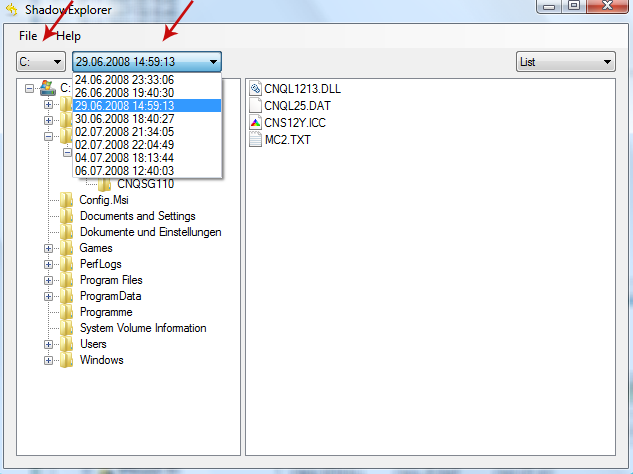
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
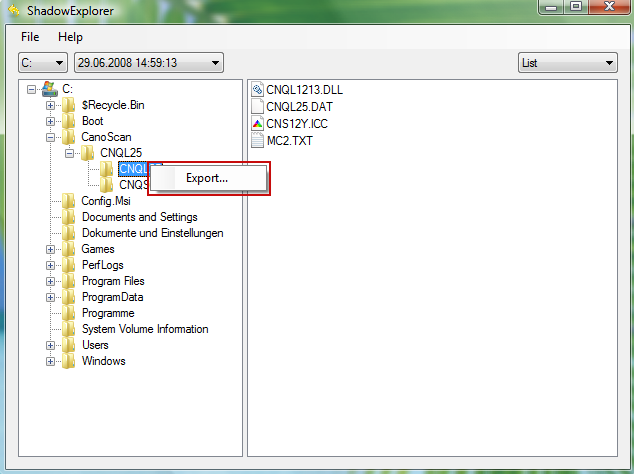
Hopefully, this will help you to restore all encrypted files or at least some of them.
Locker virus payment page:
It demands to pay 0.1 BTC and gives information on how to buy Bitcoins. There's also a payment address which is unique for every victim.
What does Locker ransomware do?
You have probably already guessed that the clue to unlocking the way ransomware works is in its name. Locker has been created to kidnap your files or data, freeze them and make them inaccessible or unusable. After doing this the program will send you an updated version of the old fashioned ransom note, demanding that you pay 0.1 BTC (about $25) for your files to be released or unlocked. Once you've paid (which, by the way, you shouldn't – more of that in a minute) you will be sent a code that allows you to unlock your encrypted files. But when we say 'you will be sent' don't take that at face value as many cyber criminals using Locker ransomware will not bother to send you anything, simply taking your money and disappearing, never to be heard of again. And don't think you'll be able to negotiate with them either – these types of people don't tend to have a customer care helpline.
And that's not all...
So that they can ensure you will be more likely to pay, victims of Locker will turn the fear factor up to eleven. You're already wondering if you're ever going to see your files and the data they contain again, but to pile even more stress upon you, many of these so called ransom notes will either tell you that they have been sent by a law enforcement agency, such as the FBI or CIA, or tell you that the unlock code will become invalid and your files destroyed if you don't pay by a certain date. In this case, cyber criminals give you 3 days to pay the ransom. The Locker ransom program says:
All your personal files on this computer are locked and encrypted by Locker [ver]. The encrypting has been done by professional software and your files such as: photos, videos, and cryptocurrency wallets are not damaged but just not readable for now. You can find the complete list with all your encrypted files in the files tab.
The encrypted files can only be unlocked by a unique 2048-bit RSA private key that is safely stored on our server till [date]. If the key is not obtained before that moment it will be destroyed and you will not be able to open your files ever again.
Obtaining your private unique key is easy and can be done clicking on the payment tab and pay a small amount of 0.1 BTC to the wallet address that was created for you. If the payment is confirmed the decryption key will be sent to your computer and the Locker software will automatically start the decrypting process. We have absolutely not interest in keeping your files encrypted forever.
You can still safely use your computer, no new files will be encrypted and no malware will be installed. When the files are encrypted Locker [ver] will automatically uninstall itself.
It's very similar to BitCryptor ransomware. It shows time remaining, lists all the encrypted files and gives you a personal Bitcoint wallet address.
What do I do? Pay the fine and make the problem go away?
It's not a good idea but if you really really care about the files, pay the ransom, although no guarantee that you'll get the files back. Besides, by paying you'll be perpetuating cyber crime. Instead, follow the removal guide below on how to salvage your data and clean your computer ASAP. There are a few tools that can help you to restore at least some of your files without paying a ransom. Even though, there's no guarantee that these tools will help you, there's also no reason not to try them out. Who knows, maybe you will be the lucky one. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
IMPORTANT! Before running anti-malware software and trying to restore your files COPY the encrypted files, your Bitcoin wallet address (see under Payment tab) and %PROGRAMDATA%\rkcl, %PROGRAMDATA%\tor, %PROGRAMDATA%\steg or %PROGRAMDATA%\Digger folder (with files) to external hard drive, CD/DVD or a USB flash key. You should have these in case you decide to pay the ransom or someone creates a decryption tool.

The ransomware is also known to disable certain system features like system restore, delete shadow copies, and prevent the uninstalling of software. This makes it incredibly difficult to remove it or roll back to solve the issue.
Step 1: Removing Locker and related malware:
Before restoring your files from shadow copies, make sure Locker virus is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
IMPORTANT! If you can't download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again. Also, try to disable bclock.exe using Process Explorer.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by Locker virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Use Locker Unlocker decryption tool. This tool is designed to decrypt files encrypted by the Locker ransom virus.
Method 4: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.

3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.

Hopefully, this will help you to restore all encrypted files or at least some of them.












