The majority of people working or playing with computers have heard of a good number of the assorted malicious software programs that are out there. We all know the threat of Trojan Horses, the sinister tactics of Spyware, the aggravating Adware and the pest that is Potentially Unwanted Programs, and let's not forget vicious viruses. However there is one type of malware that never seems to garner the same levels of notoriety as its cousins, and that is something named Ransomware. So what exactly is Crypt0L0cker ransomware and is it something that you should be overly concerned about if it's not as well known? In a word: yes. Crypt0L0cker most definitely IS something you should know a little more about, and do your utmost to protect yourself from.
Here we are going to take a closer look at what ransomware is, how it spreads itself, what it can do to your files and PC - and more importantly - how you protect yourself from becoming a victim.
How does ransomware take control of your PC?
The Crypt0L0cker (.encrypted) ransomware is spread in a number of different ways; all of them seemingly innocuous, and therefore increasing the chances of us falling prey to the malware. Sometimes this ransomware is disseminated by email attachments or in links in mails or instant messages. Just a few days ago the AFP warned about AFP traffic infringement scam that distributed this ransomware.
The Trojan dropper is detected as TR/Crypt.Xpack.197573, Trj/RansomCrypt.C and Win32:Crypt-SAR [Trj]. Some users got caught by this virus campaign and immediately noticed that all jpeg, pdf and doc files had the extension ".encrypted" after them. Other variants of this ransomware are unleashed by programs or even entire websites that have been infected by it. So what do you need to do to lower your likelihood of being attacked? You need to be careful when opening emails and instant messages – especially if you don't know the sender – and of course you should exercise extreme caution when opening attachments, images, files or links within them. You also need to be very careful when downloading apps or programs in case they have been compromised. It's hard to say that you should also watch what websites you visit, as any site can be targeted by malware but the general rule of thumb is to avoid anything that your instincts tell you is low quality or contains dubious content.
What is Crypt0L0cker's MO?
Ransomware, as you may have already guessed, exists to extract money from you in the form of a ransom. And to do this it needs to hold something hostage, in this case, your computer.
A ransomware attack paralyses your operating system, leaving you unable to open files or programs. When you try, you'll be hit with a ransom note sent by email or displayed on your screen telling you that you have been found to have downloaded illegal or pirated software or accessed a website of an illicit nature. It then demands a sum of money in return for the release of your documents or system.
Even worse, some ransomware will tell you that you are now on a watch list and about to be investigated for your alleged cyber crimes by the government or police! Clearly this is to convince you to pay the ransom, however, don't give in, but follow the steps in the removal guide below. First, you should remove the ransomware and any other related malware from your computer. Secondly, don't pay the ransom and try to restore your files with the tools listed below. If you back up your files regularly, you can retrieve some of your information, if not all of it, if your files suddenly become encrypted and have this odd *.encrypted extension. If you don't have any backups then you can try to restore at least some of your files with Shadow Explorer and other Windows system tools. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing Crypt0L0cker (.encrypted) and related malware:
Before restoring your files from shadow copies, make sure Crypt0L0cker virus is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by Crypt0L0cker (.encrypted) virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
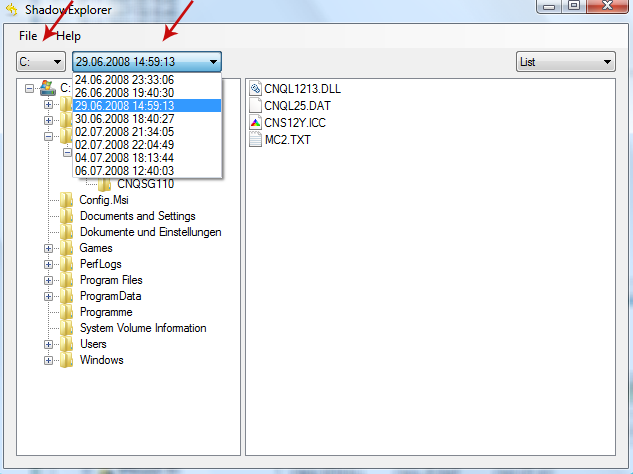
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
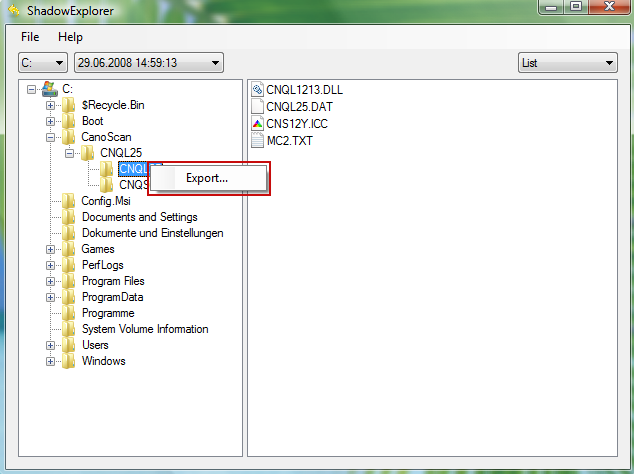
Hopefully, this will help you to restore all encrypted files or at least some of them.
Encrypted Files (.encrypted extension) Malware Removal Guide
4/
5
Oleh
soni agus



