Taking a more in depth look at .exx ransomware
Ransomware is among the types of malware that is looking to make a dent in your bank account by conning you out of your hard earned cash. In this instance it demands a ransom in return for releasing your data that it has held hostage, or the ability to use your computer.
It does a number of things to coerce you into parting with your money. Here are the most common ones:
- It can change your default browser settings so that you have trouble accessing the internet. This has the double pronged benefit (for the attacker) of not only frustrating you into paying the ransom but it also makes it harder for you to find a resolution to get rid of it.
- Ransomware can also disable your files and documents by encrypting them. As you already know, it encrypts your files and appends the .exx extension. That's the only thing you can use to identify which ransomware do you have on your computer. In other words, holding them hostage until you pay the ransom. The warning sent by the attacker, either by email or displayed on your screen, will state that they will send you a code that you can key in, in order to deactivate the ransomware and release the data. However, this is often not the case and you will be quite literally paying (a not inconsiderable amount) of money for absolutely nothing. Ransom notes are usually HELP_TO_SAVE_FILES.txt and HELP_TO_DECRYPT_YOUR_FILES.txt. You can wind the in each folder with at least one encrypted file.
- Some types of ransomware are designed to look like antivirus software and will display a pop-up warning saying that your PC is infected with a virus or malware. It will scare you into paying to install the program so that it can clean your machine. Of course, it’s not going to alert you to its own presence, so again, you will be paying for a fake scan, fake viruses, and a software program that does absolutely nothing.
So I shouldn't pay a ransom?
If you've been infected by ransomware that uses the .exx extension to make your files inaccessible, no, you really should not pay a release fee. Firstly, by giving in to cyber criminals, you are only convincing them that they are in the right line of business. Secondly, chances are, as mentioned, you are paying for thin air. There's no guarantee that they will decrypt your files. At the time I was analyzing this rabsomware, cyber criminals demanded to pay 2.2 Bitcoins which is more than $500. The decryption service can be accessed by using Web to Tor services: dlosrngis35.com, anfeua74x36.com, tor2web.blutmagie.de. Cyber criminals wrote a very detail guide on how to buy bitcoins and even made a support ticket system in case you have any questions.
How to get my files back?
If you have a recent backup, wipe your hard disk and reinstall your files. If you don't, try Shadow Explorer program or search your computer for previous versions of files. If you are lucky enough you may find files that were not encrypted and renamed to .exx. But before restoring your files, please remove the ransomware and related malware files from your computer. Otherwise, you will simply waste your time. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing .exx extension ransomware (TeslaCrypt) and related malware:
Before restoring your files from shadow copies, make sure the ransomware is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
Important! If you can't download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by .exx extension (TeslaCrypt) virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Try the TeslaCrypt Decryption Tool by Cisco. Download TeslaDecrypt tool and run it.
Method 4: Try the TeslaDecoder Decryption Tool. Download TeslaDecoder tool and run it.
Method 5: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
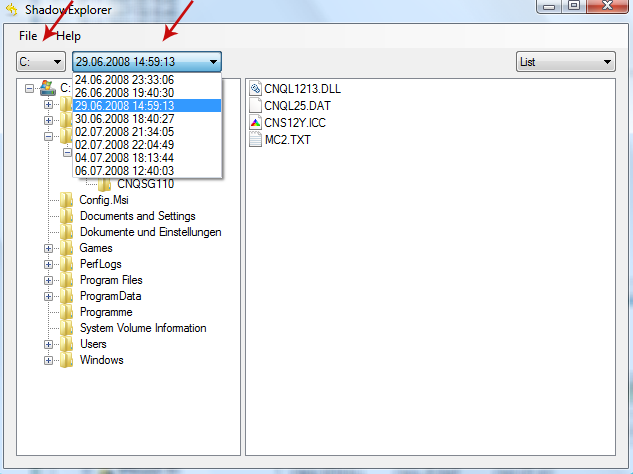
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
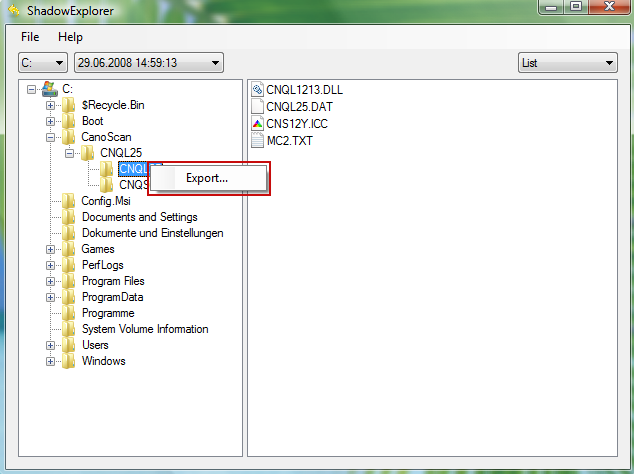
Hopefully, this will help you to restore all encrypted files or at least some of them.
Encrypted Files (.exx extension) Malware Removal Guide
4/
5
Oleh
soni agus


