Crypt0L0cker and its aliases
If you've heard of a cryptoworm, cryptoware, a cryptovirus, or a cryprotrojan then you've heard of ransomware as these are all names variously given to the same type of program. But just what exactly is cryptoware, or as we will refer to it, ransomware? As with most types of malicious software, the clue is in the name. Crypt0L0cker, as you may have already guessed, holds your computer, data or files to ransom and then attempts to extort money from you by promising to release them (or decrypt, decode, or unlock them) upon receiving payment which is at least $400.
How does Crypt0L0cker get on to your computer?
There are a couple of different ways that Crypt0L0cker is spread. You may be infected by it having paid a visit to a website that has been compromised by it, or alternatively it can hijack you through an email attachment, a link in a chat application message, or via a computer program. One thing is clear about the murky world of malware – we are at increasing risk every time we log onto our computers and onto the internet.
The ransomware Modus Operandi
As mentioned Crypt0L0cker’s MO is to kidnap your files (PDF, xml, doc, docx, xls, xlsx, just the name a few) or parts of your PC's operating system, demand payment for their release and then – maybe return them to you. And yes, we did say maybe. Let's not forget that we are dealing with an unscrupulous attacker here – chances of them bothering to send you a code to unlock your data once payment has been received are not really all that likely.
WARNING we have encrypted your files with Crypt0L0cker virus
Your important files (including those on the networks disks, USB, etc): photos, videos, documents, etc. were encrypted by Crypt0L0cker virus. The only way to get your files back is to pay us. Otherwise, your files will be lost.
How the Crypt0L0cker demands payment is via – of course – a ransom note. This will either be a text file DECRYPT_INSTRUCTIONS.txt or a HTML pop-up window DECRYPT_INSTRUCTIONS.html, or even an aggressive full screen notification. To make matters worse these ransom notes often portray the kidnapper not as a random third party but as a national, or even international, law enforcement agency. For example, the FBI if your IP address is in the United States or Scotland Yard if you are in the United Kingdom.
The 'note' state that your important files were encrypted – and that you can avoid legal consequences by paying the fine. That's complete rubbish of course. No national law enforcement agency would send such a demand, so if you receive one – whatever you do, DON'T pay it!
Now, the most important part, how to get your files back. The best method is obviously to restore your files from a recent backup. If you have been performing backups, then you should use your backups to restore your files. If you don't have backups then you can try restoring your files with a program called Shadow Explorer. It may work and or may not. I know some users managed to get at least some of their files back using this program. You can try it too. There's really nothing to lose after all. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing Crypt0L0cker and related malware:
Before restoring your files from shadow copies, make sure Crypt0L0cker virus is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by Crypt0L0cker virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
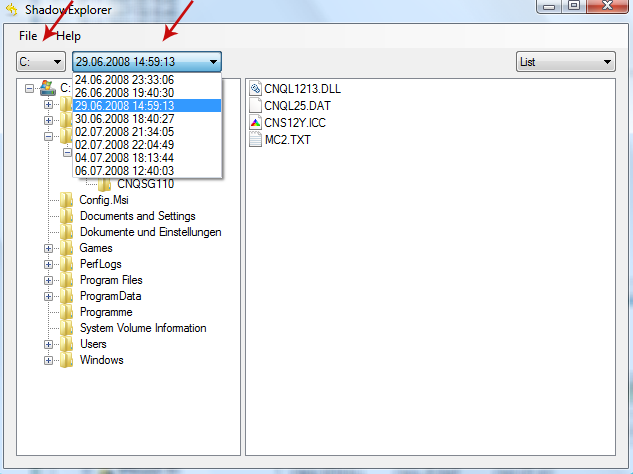
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
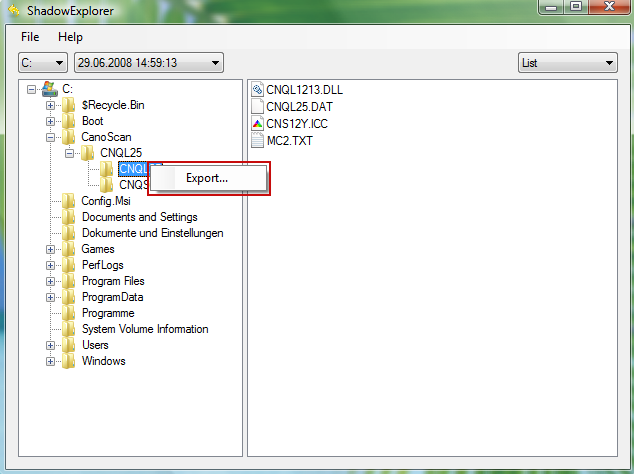
Hopefully, this will help you to restore all encrypted files or at least some of them.
How to Remove Crypt0L0cker Virus and Restore Encrypted Files
4/
5
Oleh
soni agus


