This Trojan horse can be used for a wide range of reasons and for a number of activities on the unsuspecting owner’s PC or laptop system. Once installed, a hacker can use it to execute and access files, change system configurations, set up ports, log key strokes, monitor packets on the network, collect different user names and passwords so that they can create other personas and attack other computers using the victim’s whilst remaining incognito and monitor – or spy to put it more accurately – computer usage, software downloaded and websites browsed.
So how do you tell if you’re the victim of this trojan? If you are using Norton Antivirus or any other Symantec product, you will get a warning stating that one of your files, for instance services.exe, (Trojan.Zeroaccess!inf4) detected by Virus scanner and Auto-Protect. In other words, this means that services.exe contains threat Trojan.Zeroaccess!inf4. The risk is high. Unfortunately it’s just not that easy because the very point of rootkits is that they are undetectable by the user.
What do you do if you think you have been infected? Even if a computer expert has attempted to remove Trojan.Zeroaccess!inf4 manually, it is very difficult for them to tell if it’s gone completely, therefore most of them recommend that the only way to deal with the situation is to scan the system with anti-malware software.
There is no antivirus or security software than can keep all rootkits at bay but there are a number of steps you can take to protect yourself. Enabling a firewall on your computer is an excellent idea as is ensuring that you always have the latest updates for all your installed software. If you don’t have antivirus software installed, make sure you do it now and always keep that up to date too, with the latest versions and patches. Knowing who has access to your PC or laptop is important too so you might want to consider limiting user privileges, especially if you leave it logged in in a public place, work environment or if you have shared living arrangements.
As always, exercise caution when opening email attachments and accepting file transfers over applications and be careful when clicking on links to webpages, both on the internet and in emails. Downloading pirated software is a no-no too and whether it’s for bank accounts or something as seemingly harmless as your Facebook account, always use strong passwords.
Unfortunately Trojan.Zeroaccess!inf4 and ZeroAccess rootkit being used for malicious purposes are a feature of the internet landscape however with a little care and attention we can all do our best to try and limit the eventuality of becomes victims ourselves. The following instructions will show you how to remove Trojan.Zeroaccess!inf4 from your computer. If you have any questions, please leave a comment below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Trojan.Zeroaccess!inf4 removal instructions:
1. Download recommended anti-malware software (direct download) and run a full system scan to remove Trojan from your computer.
2. Download and run TDSSKiller. Press the button Start scan for the utility to start scanning.
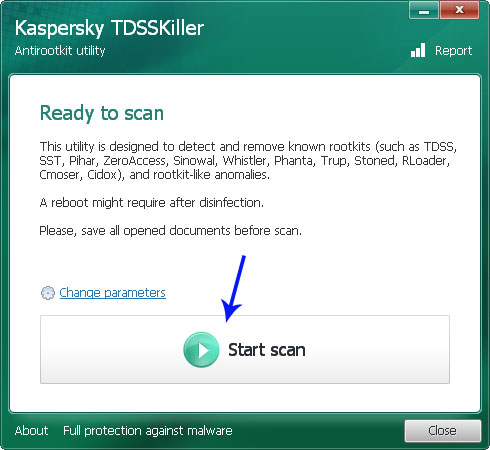
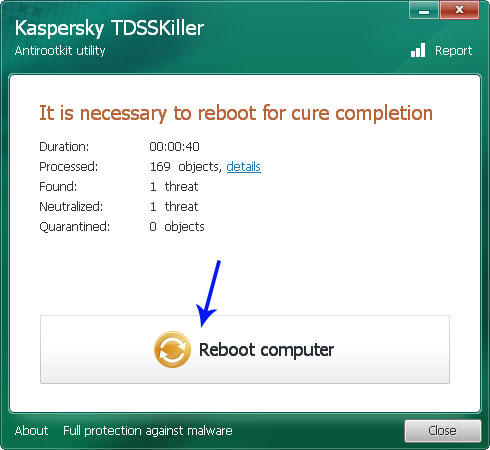
3. Wait for the scan and disinfection process to be over. Then click Continue. Please reboot your computer after the disinfection is over.
Remove Trojan.Zeroaccess!inf4 (Uninstall Guide)
4/
5
Oleh
soni agus

