Outbound Traffic Detected. Is My Computer Infected?
Security AdvisoriesIf you spend any considerable amount of time online, whether you are browsing the internet for fun or you are using it for work, then you really need to be well aware of the different risks that you face. The amount of viruses, malware, and other parasites and scams make using the internet a little like taking a walk through a mine field. And the problem is only compounded by the fact that because there is good money to be made in this area, there are constant upgrades being released to existing threats, and new and different ones springing up all the time. Outbound Traffic Detected pop-up message usually means that your anti-virus program has detected a large amount of suspicious outbound traffic on your system. In other words, there are malicious programs on your computer that somehow got slip through undetected and now try to establish remote connection with C&C servers or even worse - send sensitive information to cyber criminals. Most of the time, outbound traffic is being sent by Trojan horse malware.
So stay one step ahead of just one of these types of malicious software by learning a little more about something called a Trojan Horse.
If you keep getting "Outbound Traffic Detected" pop-up message then your computer is probably infected with malware, most likely a Trojan horse. This is a particularly vicious type of malware that has been created with the aim of causing you maximum disruption and, often irreversible, harm. Trojan Horse malware is very sneaky when it comes to installation tactics and it uses you and your trusting nature to give it an unwitting helping hand. To say a Trojan Horse infection is inconvenient is to do it a disservice and it is something which can have a lasting effect on both you and your computer.
Trojan Horse tactics
Trojan Horses can infect you in a number of different ways. They might be an attachment in an email, or a link or file sent by instant message. They can also be hiding in a program or application that you downloaded thinking it was harmless. A Trojan Horse programmer fools you into opening and installing or downloading their malware by encouraging you to believe that is innocent. It might be disguised as a fun game, a useful lifestyle app. And if you stop a moment to think about it, you'll see the pattern and understand where the malware got both its inspiration and its name from.
Just like the huge wooden horse built by the ancient Greeks as a ploy to hide their soldiers in and convince their enemies, the Trojans to accept beyond their city gates, a modern day Trojan is something which plays on its victims' naivety to attack them from within. Here's an example of a message you can get when a Trojan horse or other malware tries to send outbound traffic:
In this case it's Security Request Norton Outbound Traffic Detected message but yours might be different (depends on your anti-virus). The problem is that even if you re run the program it comes up that everything is OK. As a result, you need to use anti-malware software to remove malware that your anti-virus misses. Thankfully, there are a few tools specifically designed to detected malware which is sending out outbound traffic.
What will a Trojan Horse program do when it has been installed on your PC?
Needless to say, it will send outbound traffic on your computer. But it really has one goal in mind and that is, once it has hijacked your PC, it will begin to attack you from the inside. Trojan malware particularly likes to encrypt files, data and documents, making them inaccessible while the infection is on your machine. Some Trojans even take this one step further by going straight for the jugular and simply destroying files and data from the get go.
Trojan Horse malicious software and Outbound Traffic: a conclusion
Trojan Horses and other malware are a lot nastier than a lot of the other types of malware that you might have read about so make sure you download a great anti-malware program and do everything you can to protect your PC from this thoroughly unpleasant malware. If your computer is already infected and you can't seem to get rid of this dangerous malware, please follow the steps in the removal guide below. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
1. First of all, download anti-malware software and run a full system scan. It will detect and remove this infection from your computer. You may then follow the manual removal instructions below to remove the leftover traces of this malware. Hopefully you won't have to do that.
NOTE: If you are using Internet Explorer and can't download anti-malware software because "Your current security settings do not allow this file to be downloaded" then please reset IE security settings and try again.
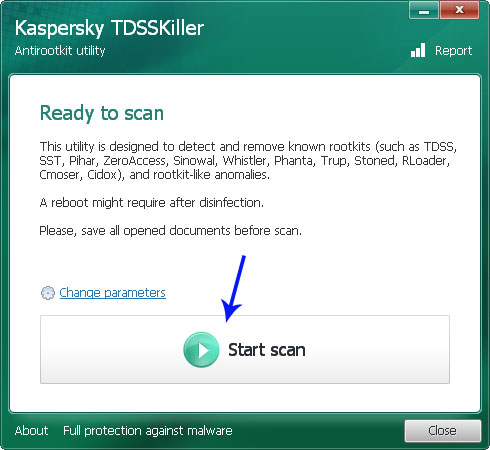
2. Download and run TDSSKiller. Press the button Start scan for the utility to start scanning.
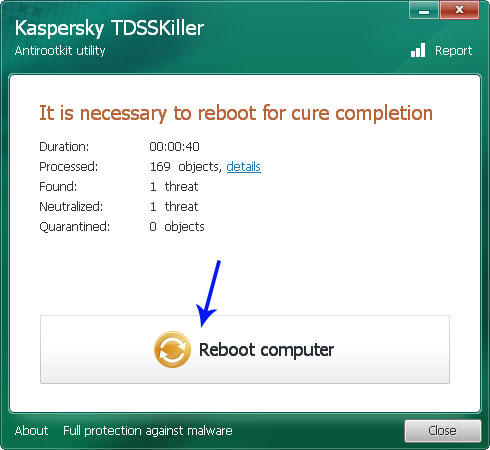
3. Wait for the scan and disinfection process to be over. Then click Continue. Please reboot your computer after the disinfection is over.
So stay one step ahead of just one of these types of malicious software by learning a little more about something called a Trojan Horse.
If you keep getting "Outbound Traffic Detected" pop-up message then your computer is probably infected with malware, most likely a Trojan horse. This is a particularly vicious type of malware that has been created with the aim of causing you maximum disruption and, often irreversible, harm. Trojan Horse malware is very sneaky when it comes to installation tactics and it uses you and your trusting nature to give it an unwitting helping hand. To say a Trojan Horse infection is inconvenient is to do it a disservice and it is something which can have a lasting effect on both you and your computer.
Trojan Horse tactics
Trojan Horses can infect you in a number of different ways. They might be an attachment in an email, or a link or file sent by instant message. They can also be hiding in a program or application that you downloaded thinking it was harmless. A Trojan Horse programmer fools you into opening and installing or downloading their malware by encouraging you to believe that is innocent. It might be disguised as a fun game, a useful lifestyle app. And if you stop a moment to think about it, you'll see the pattern and understand where the malware got both its inspiration and its name from.
Just like the huge wooden horse built by the ancient Greeks as a ploy to hide their soldiers in and convince their enemies, the Trojans to accept beyond their city gates, a modern day Trojan is something which plays on its victims' naivety to attack them from within. Here's an example of a message you can get when a Trojan horse or other malware tries to send outbound traffic:
In this case it's Security Request Norton Outbound Traffic Detected message but yours might be different (depends on your anti-virus). The problem is that even if you re run the program it comes up that everything is OK. As a result, you need to use anti-malware software to remove malware that your anti-virus misses. Thankfully, there are a few tools specifically designed to detected malware which is sending out outbound traffic.
What will a Trojan Horse program do when it has been installed on your PC?
Needless to say, it will send outbound traffic on your computer. But it really has one goal in mind and that is, once it has hijacked your PC, it will begin to attack you from the inside. Trojan malware particularly likes to encrypt files, data and documents, making them inaccessible while the infection is on your machine. Some Trojans even take this one step further by going straight for the jugular and simply destroying files and data from the get go.
Trojan Horse malicious software and Outbound Traffic: a conclusion
Trojan Horses and other malware are a lot nastier than a lot of the other types of malware that you might have read about so make sure you download a great anti-malware program and do everything you can to protect your PC from this thoroughly unpleasant malware. If your computer is already infected and you can't seem to get rid of this dangerous malware, please follow the steps in the removal guide below. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
"Outbound Traffic Detected" Malware Removal Guide:
1. First of all, download anti-malware software and run a full system scan. It will detect and remove this infection from your computer. You may then follow the manual removal instructions below to remove the leftover traces of this malware. Hopefully you won't have to do that.
NOTE: If you are using Internet Explorer and can't download anti-malware software because "Your current security settings do not allow this file to be downloaded" then please reset IE security settings and try again.
2. Download and run TDSSKiller. Press the button Start scan for the utility to start scanning.

3. Wait for the scan and disinfection process to be over. Then click Continue. Please reboot your computer after the disinfection is over.






