How to remove IronDefender (Uninstall Guide)
Rogue programsIronDefender is a rogue security program that masquerades as a legitimate malware removal tool and claims that your computer is infected with worms, dialers, Trojans, spyware and other malicious software. The main goal of this fale software is to deceive you into thinking that your computer is infected with malware. Once installed, IronDefender will pretend to scan your computer for viruses. Then it will give false or exaggerated reports of threats on your computer and state that you should pay for a full version of the program to remove these threats and to proetct your computer against viruses and other security threats. Please don't purchase it and remove IronDefender from the system as soon as possible. If you find that your computer is infected with this malware please follow the removal instructions below.

Iron Defender is promoted mostly through the use of fake online anti-malware scanners. We got the sample of this rogue from the fake online scanner as well. Most of the time this scareware has to be manually installed, but in some cases it might be downlaoded and installed without your knowledge through the use of Trojans downloaders. These Trojans are distributed in various ways, spam e-mails, misleading social engineering schemes, infected web pages or files. While running, IronDefender will display fake security warnings and notifications about critical spyware objects, cyber thieves, password stealing Trojans and other threats.



Furthermore, the rogue program will display its Security Center pop-up which impersonates the legitimate Windows Security Center. The fake Security Center will claim that your computer is unprotected against viruses. It will state that you should install an anti-virus software which is IronDefender of course.

If you choose to buy this rogue program it will take you to its billing page. As you can see in the image below, Iron Defender costs $49.95.

The rogue program also displays a pop-up that leads to flvdirect.com (please don't visit this website).

IronDefender is from the same family as ArmorDefender.
Last, but not least, IronDefender may block legitimate anti-spyware and anti-virus programs and disable certain system utilities, task manager, registry editor and system restore. As you can see, it's nothing more but a scam. If you have already bought it then please contact your credit card company and dispute the charges. Finaly, please follow the removal instructions below to remove IronDefender from your computer using legitimate anti-malware software. If you have any questions or addtional information about this misleading program please leave a comment. Good luck and be safe online!
IronDefender removal instructions (in Safe Mode with Networking):
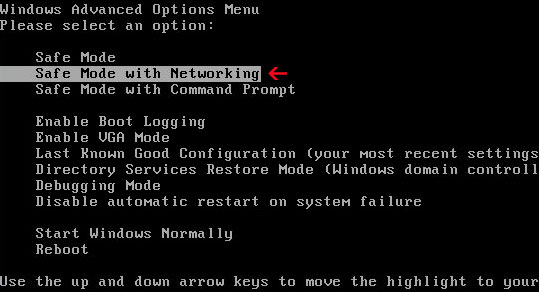
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Download anti-malware software from the list below and run a full system scan.
NOTE: before saving the selected program onto your computer, please rename the installer to iexplore.exe or winlogon.exe. With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
3. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
IronDefender removal instructions in Normal mode:
1. Download Process Explorer iexplore.exe. Double click to open it. Look for IronDefender in the process list and terminate its process(es): F0E84.exe and gen4436.exe.
2. Download anti-malware software from the list below. Update it and run a full system scan.
NOTE: before saving the selected program onto your computer, please rename the installer to iexplore.exe or winlogon.exe. With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
3. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
IronDefender associated files and registry values:
Files:
In Windows XP:

Iron Defender is promoted mostly through the use of fake online anti-malware scanners. We got the sample of this rogue from the fake online scanner as well. Most of the time this scareware has to be manually installed, but in some cases it might be downlaoded and installed without your knowledge through the use of Trojans downloaders. These Trojans are distributed in various ways, spam e-mails, misleading social engineering schemes, infected web pages or files. While running, IronDefender will display fake security warnings and notifications about critical spyware objects, cyber thieves, password stealing Trojans and other threats.
Spyware Alert!
Your computer is infected with spyware. It could damage your critical files or expose your provate data on the Internet. Click here to register your copy of IronDefender and remove spyware threats from your PC.

Security Center Alert!
Infiltration Alert!
Your computer is being attacked by an Internet virus. It could be a passwrod-stealing attack, a trojan-dropper or similar.
Threat: Crypter-file

733 SPYWARE Found
Attention: DANGER!
IronDefender has detected 733 Critical SPYWARE Objects while scanning the system.

Furthermore, the rogue program will display its Security Center pop-up which impersonates the legitimate Windows Security Center. The fake Security Center will claim that your computer is unprotected against viruses. It will state that you should install an anti-virus software which is IronDefender of course.

If you choose to buy this rogue program it will take you to its billing page. As you can see in the image below, Iron Defender costs $49.95.

The rogue program also displays a pop-up that leads to flvdirect.com (please don't visit this website).

IronDefender is from the same family as ArmorDefender.
Last, but not least, IronDefender may block legitimate anti-spyware and anti-virus programs and disable certain system utilities, task manager, registry editor and system restore. As you can see, it's nothing more but a scam. If you have already bought it then please contact your credit card company and dispute the charges. Finaly, please follow the removal instructions below to remove IronDefender from your computer using legitimate anti-malware software. If you have any questions or addtional information about this misleading program please leave a comment. Good luck and be safe online!
IronDefender removal instructions (in Safe Mode with Networking):
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm

NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Download anti-malware software from the list below and run a full system scan.
NOTE: before saving the selected program onto your computer, please rename the installer to iexplore.exe or winlogon.exe. With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
3. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
IronDefender removal instructions in Normal mode:
1. Download Process Explorer iexplore.exe. Double click to open it. Look for IronDefender in the process list and terminate its process(es): F0E84.exe and gen4436.exe.
2. Download anti-malware software from the list below. Update it and run a full system scan.
NOTE: before saving the selected program onto your computer, please rename the installer to iexplore.exe or winlogon.exe. With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
3. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
IronDefender associated files and registry values:
Files:
In Windows XP:
- C:\Program Files\FDFCA\F0E84.exe
- C:\Program Files\FDFCA\Uninstall.exe
- C:\Documents and Settings\Administrator\Local Settings\Temp\gen4436.exe
- C:\WINDOWS\[RANDOM CHARACTERS].exe
- C:\WINDOWS\[RANDOM CHARACTERS].bin
- C:\WINDOWS\[RANDOM CHARACTERS].dll
- C:\WINDOWS\[RANDOM CHARACTERS].cpl
- C:\WINDOWS\system32\[RANDOM CHARACTERS].exe
- C:\WINDOWS\system32\[RANDOM CHARACTERS].bin
- C:\WINDOWS\system32\[RANDOM CHARACTERS].dll
- C:\WINDOWS\system32\[RANDOM CHARACTERS].cpl
- C:\Program Files\FDFCA\F0E84.exe
- C:\Program Files\FDFCA\Uninstall.exe
- C:\Users\[User Name]\Local Settings\Temp\gen4436.exe
- C:\WINDOWS\[RANDOM CHARACTERS].exe
- C:\WINDOWS\[RANDOM CHARACTERS].bin
- C:\WINDOWS\[RANDOM CHARACTERS].dll
- C:\WINDOWS\[RANDOM CHARACTERS].cpl
- C:\WINDOWS\system32\[RANDOM CHARACTERS].exe
- C:\WINDOWS\system32\[RANDOM CHARACTERS].bin
- C:\WINDOWS\system32\[RANDOM CHARACTERS].dll
- C:\WINDOWS\system32\[RANDOM CHARACTERS].cpl
- HKEY_CURRENT_USER\Software\IronDefender
- HKEY_LOCAL_MACHINE\software\microsoft\Internet Explorer\ActiveX Compatibility\{188D171F-A126-4A3B-B1DC-ED698FDFCADA}
- HKEY_LOCAL_MACHINE\software\microsoft\Windows\CurrentVersion\Run "F0E84.exe"
- HKEY_LOCAL_MACHINE\software\microsoft\Windows\CurrentVersion\Uninstall\IronDefender
- HKEY_USERS\current\software "C:\Program Files\FDFCA\"

















