Antivirus Security Pro Virus Removal Guide
Rogue programsAntivirus Security Pro is a form of malware and besides not doing what it says it will do, i.e. protecting your computer from…er…malware, in the more unpleasant scenarios it can actually infect your PC with even more unwanted software. It belongs to the Win32/Winwebsec malware family.
Scareware or rogueware, as it is also known, is slippery. It makes you think you need it when you don’t and just like the product itself its makers are equally cunning in their ways to ensure that it ends up installed on their victim’s machines.
Once it’s been installed on your computer you will then notice that you keep getting pop-up windows that tell you that you have this amount of unwanted items slowing your computer down or that you have that amount of viruses or malwares infecting your system. This window will very nicely ask you if you would like it to run a scan so it can tell you exactly what these problems are. You’re worried so you click ‘yes’ or ‘run scan’, then you sit back and wait as the software does…absolutely nothing (although it may show you a fake screen that looks like it’s scanning your files).
Once the pretend scan has taken place you’ll then be told that, yes, you have lots of potentially harmful issues on your PC and to remove them all you need to do is to enter your credit card details to upgrade to the full version of the security software. It’s the perfect scam – it plays on your vulnerabilities by making up fake issues and then offers you an instant solution. Only, you have to pay for that solution – and for those of us who have been sent into panic mode thinking that our online security is being compromised or that our files are going to be corrupted, it may well seem worth entering our payment details to make the 'problems' go away there and then.
When running, Antivirus Security Pro will display fake security alerts warning you about suspicious activities and dangerous network attacks. Less computer-savvy users may think these security warnings are coming from Windows security. After all, they do look quite convincing. However, most of the time, Antivirus Security Pro changes security settings and disables Windows security center.
It will also block your web browser saying that it's infected with Conflicker and similar malware.
What is more, this rogue can close other applications, modify security settings, block access to specific websites and even download additional malware onto your computer. To remove Antivirus Security Pro virus and related malware from your computer, please follow the removal instructions below. If you have any questions, please leave a comment below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Method 1: Antivirus Security Pro virus removal using activation key:
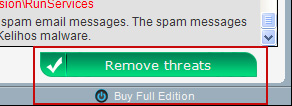
1. Open Antivirus Security Pro scanner window. Click the "Buy Full Edition" link in lower right hand corner of the scanner window or simply choose to "Remove threats".
You should now see the payment page. Click "I already have activation key".
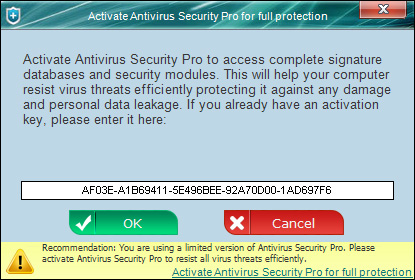
Enter the Antivirus Security Pro activation key given below and click "OK" to activate the rogue security program. Don't worry, this is completely legal since it's not genuine software.
AF03E-A1B69411-5E496BEE-92A70D00-1AD697F6
Once this is done, you are free to install recommended anti-malware software and remove Antivirus Security Pro virus from your computer.
2. Download recommended anti-malware software and run a full system scan to remove this malware from your computer.
Method 2: Antivirus Security Pro virus removal in Safe Mode with Networking:
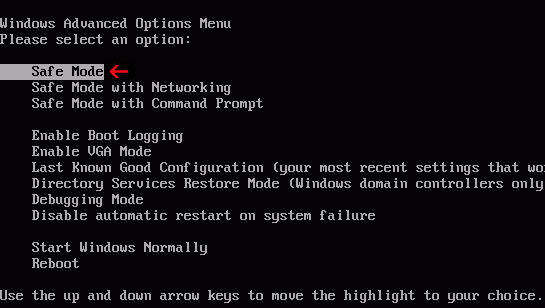
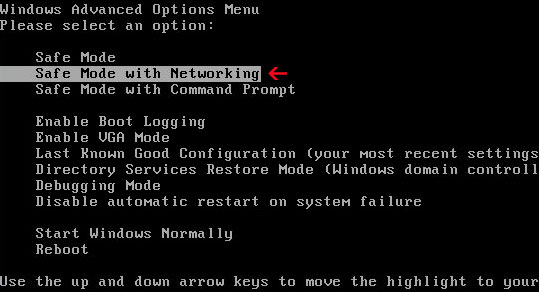
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key.
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Download recommended anti-malware software and run a full system scan to remove this malware from your computer.
Associated Antivirus Security Pro files:
Files:
Scareware or rogueware, as it is also known, is slippery. It makes you think you need it when you don’t and just like the product itself its makers are equally cunning in their ways to ensure that it ends up installed on their victim’s machines.
Once it’s been installed on your computer you will then notice that you keep getting pop-up windows that tell you that you have this amount of unwanted items slowing your computer down or that you have that amount of viruses or malwares infecting your system. This window will very nicely ask you if you would like it to run a scan so it can tell you exactly what these problems are. You’re worried so you click ‘yes’ or ‘run scan’, then you sit back and wait as the software does…absolutely nothing (although it may show you a fake screen that looks like it’s scanning your files).
Once the pretend scan has taken place you’ll then be told that, yes, you have lots of potentially harmful issues on your PC and to remove them all you need to do is to enter your credit card details to upgrade to the full version of the security software. It’s the perfect scam – it plays on your vulnerabilities by making up fake issues and then offers you an instant solution. Only, you have to pay for that solution – and for those of us who have been sent into panic mode thinking that our online security is being compromised or that our files are going to be corrupted, it may well seem worth entering our payment details to make the 'problems' go away there and then.
When running, Antivirus Security Pro will display fake security alerts warning you about suspicious activities and dangerous network attacks. Less computer-savvy users may think these security warnings are coming from Windows security. After all, they do look quite convincing. However, most of the time, Antivirus Security Pro changes security settings and disables Windows security center.
It will also block your web browser saying that it's infected with Conflicker and similar malware.
What is more, this rogue can close other applications, modify security settings, block access to specific websites and even download additional malware onto your computer. To remove Antivirus Security Pro virus and related malware from your computer, please follow the removal instructions below. If you have any questions, please leave a comment below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Method 1: Antivirus Security Pro virus removal using activation key:
1. Open Antivirus Security Pro scanner window. Click the "Buy Full Edition" link in lower right hand corner of the scanner window or simply choose to "Remove threats".

You should now see the payment page. Click "I already have activation key".
Enter the Antivirus Security Pro activation key given below and click "OK" to activate the rogue security program. Don't worry, this is completely legal since it's not genuine software.
AF03E-A1B69411-5E496BEE-92A70D00-1AD697F6

Once this is done, you are free to install recommended anti-malware software and remove Antivirus Security Pro virus from your computer.
2. Download recommended anti-malware software and run a full system scan to remove this malware from your computer.
- Malwarebytes Anti-Malware
- SUPERAntispyware
- Spybot S&D
Method 2: Antivirus Security Pro virus removal in Safe Mode with Networking:
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key.

NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Download recommended anti-malware software and run a full system scan to remove this malware from your computer.
- Malwarebytes Anti-Malware
- SUPERAntispyware
- Spybot S&D
Associated Antivirus Security Pro files:
Files:
- %CommonAppData%\UpEoq3B1\
- %CommonAppData%\UpEoq3B1\DD1
- %CommonAppData%\UpEoq3B1\UpEoq3B1.exe
- %CommonAppData%\UpEoq3B1\UpEoq3B1.exe.manifest
- %CommonAppData%\UpEoq3B1\UpEoq3B1.ico
- %CommonAppData%\UpEoq3B1\UpEoq3B1kassgxDq.in
- %CommonAppData%\UpEoq3B1\UpEoq3B1kassgxDq.lg
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "AA2014" = "%CommonAppData%\UpEoq3B1\UpEoq3B1.exe"