How to remove Security Tool virus from a computer?
Rogue programsSecurity Tool is a widely spread fake anti-virus application that was first noticed on September 2009. We receive many e-mails from people asking "How do I remove Security Tool?" or "Help with removing Security Tool!". This virus is usually promoted via fake online scanners, fake video websites, using social engineering or other misleading methods. Once installed, it simulates a system scan and states that your computer is infected with malware. That's of course a big lie, because Security Tool is an infection itself and can't properly detect any other infections. Remove this bogus software from your PC as soon as possible. Please read removal instructions below. And remember, DO NOT buy this software. If you have already done that, contact your bank/credit card company immediately and dispute the charges.

The biggest problems about this malware are:


Quick removal recommendations: first of all, try to boot your PC is Safe Mode with Networking and run a system scan with an anti-malware applicaton. If you can't do that, then you will have to end Security Tool process before doing enything else. Please follow Security Tool removal instructions below.
SecurityTool files:
Step by step Security Tool removal instructions:
Method #1
1. Download iexplore.exe (NOTE: iexplore.exe file is renamed HijackThis tool from TrendMicro).
Launch the iexplore.exe and click "Do a system scan only" button. If you can't open iexplore.exe file then download explorer.scr and run it.
2. Look for similar line in the scan results:
O4 – HKLM\..\Run: [24025916] C:\Documents and Settings\All Users\Application Data\24025916\24025916.exe
The process name will be different in your case [SET OF RANDOM NUMBERS].exe, located in:
C:\Documents and Settings\[User Name]\Local Settings\Application Data\ for Windows XP
C:\Users\[User Name]\AppData\Local\Application Data\ for Windows Vista & 7
Select all similar entries and click once on the "Fix checked" button. Close HijackThis tool.
OR you may download Process Explorer and end Antivirus Action process:
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
4. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
------------
Method #2
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm
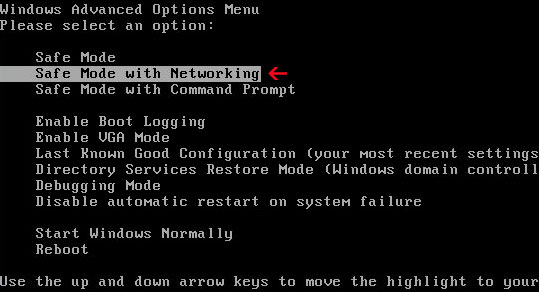
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
3. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
Bootable Rescue Disk
If your PC doesn't start up or you see just a black/blue screen and can't do anything, a bootable rescue disk may be your last chance before doing a clean installation of Windows.
Useful suggestions from other people:
"I got rid of it within a few hours by restarting my computer and while it was reloading i quickly jumped into the task manager and stopped the process by clicking on the number."
"Start up PC in safe mode, hit F8 when pc starts up, then do a system restore"
"Go to C:\Documents and Settings\All Users\Application Data
Then click Tools at the top of the page, select Folder Options, go to View and scroll down and click Show Hidden files.
Now look for a random 8 digit number. Rename the file and the 8 digit number to anything, then restart your computer and tehn go to that file and simply delete it."
More information about how to get rid of Security Tool virus:
http://answers.yahoo.com/question/index?qid=20091230193816AAeaWyN
http://answers.yahoo.com/question/index?qid=20091213183432AAGvM5j
Security Tool removal video:

The biggest problems about this malware are:
- It blocks anti-malware and anti-virus software
- Security Tool process name is randomly generated (different on each infected PC)
- Disables Windows OS system tools: Task Manager, Registry Editor and etc.
Security Tool Warning
Security Tool has detected harmful software in your system.
We strongly recommended you to register Security Tool to
remove these threats immediately.

Security Tool Warning
Your PC is still infected with dangerous viruses. Active
antivirus protection to prevent data loss and avoid the theft
of your credit card details.
Click here to activate protection.

Quick removal recommendations: first of all, try to boot your PC is Safe Mode with Networking and run a system scan with an anti-malware applicaton. If you can't do that, then you will have to end Security Tool process before doing enything else. Please follow Security Tool removal instructions below.
SecurityTool files:
- C:\Documents and Settings\[User Name]\Local Settings\Application Data\[SET OF RANDOM NUMBERS].exe
- For example:
- C:\Documents and Settings\Steve\Local Settings\Application Data\24025916.exe (for Windows XP users)
- C:\User\Steve\Local Settings\Application Data\24025916.exe (for Windows Vista & Windows 7 users)
- %UserProfile%\Desktop\Security Tool.lnk
- %UserProfile%\Start Menu\Programs\Security Tool.lnk
- HKEY_CURRENT_USER\Software\Security Tool
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run "24025916"
Step by step Security Tool removal instructions:
Method #1
1. Download iexplore.exe (NOTE: iexplore.exe file is renamed HijackThis tool from TrendMicro).
Launch the iexplore.exe and click "Do a system scan only" button. If you can't open iexplore.exe file then download explorer.scr and run it.
2. Look for similar line in the scan results:
O4 – HKLM\..\Run: [24025916] C:\Documents and Settings\All Users\Application Data\24025916\24025916.exe
The process name will be different in your case [SET OF RANDOM NUMBERS].exe, located in:
C:\Documents and Settings\[User Name]\Local Settings\Application Data\ for Windows XP
C:\Users\[User Name]\AppData\Local\Application Data\ for Windows Vista & 7
Select all similar entries and click once on the "Fix checked" button. Close HijackThis tool.
OR you may download Process Explorer and end Antivirus Action process:
- [SET OF RANDOM NUMBERS].exe, i.e. 24025916.exe
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
4. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
------------
Method #2
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm

NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
3. New threats appear every day. In order to protect your PC from such (new) infections we strongly recommend you to use ESET Smart Security.
Bootable Rescue Disk
If your PC doesn't start up or you see just a black/blue screen and can't do anything, a bootable rescue disk may be your last chance before doing a clean installation of Windows.
Useful suggestions from other people:
"I got rid of it within a few hours by restarting my computer and while it was reloading i quickly jumped into the task manager and stopped the process by clicking on the number."
"Start up PC in safe mode, hit F8 when pc starts up, then do a system restore"
"Go to C:\Documents and Settings\All Users\Application Data
Then click Tools at the top of the page, select Folder Options, go to View and scroll down and click Show Hidden files.
Now look for a random 8 digit number. Rename the file and the 8 digit number to anything, then restart your computer and tehn go to that file and simply delete it."
More information about how to get rid of Security Tool virus:
http://answers.yahoo.com/question/index?qid=20091230193816AAeaWyN
http://answers.yahoo.com/question/index?qid=20091213183432AAGvM5j
Security Tool removal video:




