It's a rather new variant first detected about a week ago. However, it doesn't bring anything new and instead use a well known encryption and extortion scheme. If you're a savvy internet user and you are well aware that there are numerous threats to your online safety. Whether you are a home user who uses the web for sending emails, shopping and reading the news or you’re a small business owner or manager, protecting the data that is rightfully yours is more crucial than ever before. And if you are the owner of a company, data security is often a matter of law and you will need to be compliant to avoid risking fines or other penalties.
It may appear that cyber criminals, hackers, phishers, spammers, call them what you will, only target big corporations, but the fact is you and your home PC or small business computer network are a far easier target. These people exploit our vulnerabilities and our lesser degree of technical expertise to make big bucks. And one of the ways they do this is through the use of a malicious software program, called ransomware.
What is help-file-decrypt.enc ransomware?
It is a program which has been designed to 'kidnap' your files or data by making them inaccessible to you. The files will be encrypted – i.e. held hostage – and only released back to you once you have paid the ransom. The ransom note pronk.txt will either be created in each folder with at least one encrypted file or displayed in a pop-up window or full screen message – pretty panic inducing for most of us. The message will tell you that once you have paid the kidnapper's demands, you will be sent a code so that you can decrypt your files. It allocates virtual memory in foreign processes and creates even more malicious files on your computer. It can also modify proxy settings and communicate with C&C servers. Not to mention that it can control your CPU usage and send sensitive information to cyber criminals.
Ransomware's method of attack
Like most malware, it is disseminated either by email, by being embedded on a compromised or malicious website, or included as an add-on with a download. And of course, as we all use email and the web every day, and download apps, software and files on a frequent basis, we are all at risk of potentially losing, not only our files, but a large sum of money too.
The trick is to stay vigilant
Just because you're not a world famous pop star or a global leader it doesn't mean you are not at risk of kidnapping – at least not this form of online cyber kidnapping anyway. Your data is just as prone to being kidnapped and held to ransom as that belonging to the most beloved film stars and loathed politicians! And that means that you need to be careful when downloading and installing things, and be very cautious when dealing with emails or chat messages from unknown senders.
You should also try to avoid visiting websites that may potentially be disreputable, and don't let yourself be suckered into downloading freebie games and apps that don't have any reviews or recommendations or are not offered via one of the big download websites.
Of course, installing a good anti-malware program on your PC is crucial too, as is making sure it is always up to date.
How to get my files back?
If you have a recent backup, wipe your hard disk and reinstall your files. If you don't, try Shadow Explorer program or search your computer for previous versions of files. If you are lucky enough you may find files that were not encrypted. But before restoring your files, please remove the help-file-decrypt.enc ransomware and related malware files from your computer. To do so, please follow the steps in the removal guide below. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing help-file-decrypt.enc (Trojan.Cryptolocker.X) virus and related malware:
Before restoring your files from shadow copies, make sure the Trojan.Cryptolocker.X is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
Important! If you can't download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by help-file-decrypt.enc (Trojan.Cryptolocker.X) virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
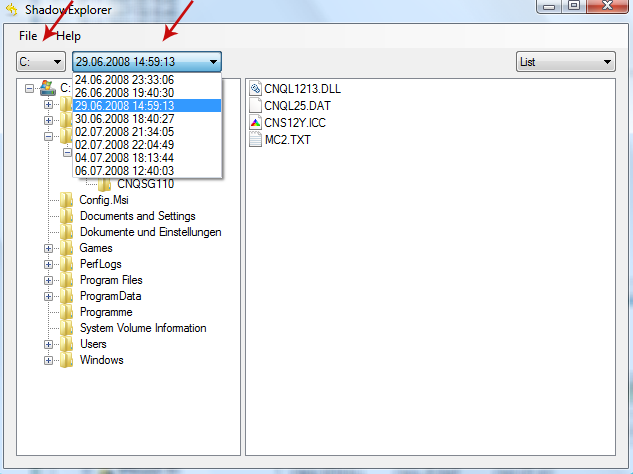
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
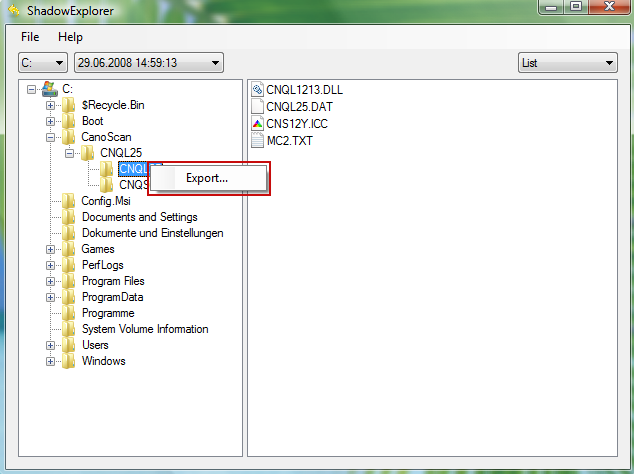
Hopefully, this will help you to restore all encrypted files or at least some of them.
Remove help-file-decrypt.enc Virus and Restore Encrypted Files
4/
5
Oleh
soni agus

