Decoder@tutamail.com ransomware is a particularly unpleasant type of malicious software (not that any types of malware are anything to relish being infected by...) But unlike some of the malware programs which will show you adverts or redirect your internet searches – adware and Potentially Unwanted Programs we’re looking at you - ransomware is a program that can cause you real distress, delete or damage your personal files – and even wind up costing you a fair amount of money. Here's an example of how an encrypted Word file is listed in a folder:
tasks-aug.docx.id-5874213680_decoder@tutamail.com
As you can see, the original file name is tasks-aug.docx. The encoder virus encrypted it and added a unique id, in this case 5874213680, and an email address decoder@tutamail.com that should be used to contact cyber criminals and receive further steps on how to get your files back. They also mentioned decoder@mailfence.com in a ransom note in case the main one doesn't work or you don't receive a response within 48 hours. What is more, it's not longer and .docx file but an executable file. This ransomware changes file extension for who knows what reasons because when a file is encrypted the extension isn't important.
Sounds nasty – just what is this ransomware?
It has been designed with one aim in mind: to make money. Not only that but it does so by preying on our fears and vulnerabilities. As the name suggests, ransomware infects your PC then holds your files, photos, documents, etc, etc, hostage. It normally encrypts them so you have no chance of breaking the code and accessing them while it is on your machine. It then demands that you pay a ransom in return for the decryption code that will release your files. However one thing to bear in mind if you do get hit by ransomware is that there are numerous tales of people parting with their cash only to receive no code whatsoever. And it's not like you are going to be able to call a ransomware programmer's helpline to ask for assistance, is it? Although, you can email them.
Other ways ransomware gets you to pay a fine
As well as holding your documents to ransom, decoder@tutamail.com ransomware can also change your default browser settings so that accessing the internet is virtually impossible. Of course, this is unacceptable as the vast majority of us need the web to be able to do our jobs and, increasingly, live our lives. How long do you think you'd last without the internet on your computer? Would you crack and simply pay the ransom?
How to get my files back?
If you have a recent backup, wipe your hard disk and reinstall your files. If you don't, try Shadow Explorer program or search your computer for previous versions of files. If you are lucky enough you may find files that were not encrypted. But before restoring your files, please remove the ransomware and related malware files from your computer. To do so, please follow the steps in the removal guide below. If you have any questions, please leave a comment down below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Step 1: Removing decoder@tutamail.com encoder virus and related malware:
Before restoring your files from shadow copies, make sure the Encoder Virus is not running. You have to remove this malware permanently. Thankfully, there are a couple of anti-malware programs that will effectively detect and remove this malware from your computer.
1. First of all, download and install recommended anti-malware scanner. Run a full system scan and remove detected malware.
Important! If you can't download or run it, please restart your computer in Safe Mode with Networking or Safe Mode and try again.
2. Then, download ESET Online Scanner and run a second scan to make sure there are no other malware running on your computer.
That's it! Your computer should be clean now and you can safely restore your files. Proceed to Step 2.
Step 2: Restoring files encrypted by encoder virus:
Method 1: The first and best method is to restore your files from a recent backup. If you have been regularly performing backups, then you should use your backups to restore your files.
Method 2: Try to restore previous versions of files using Windows folder tools. To learn more, please read Previous versions of files.
Method 3: Using the Shadow Volume Copies:
1. Download and install Shadow Explorer. Note, this tool is available with Windows XP Service Pack 2, Windows Vista, Windows 7, and Windows 8.
2. Open Shadow Explorer. From the drop down list you can select from one of the available point-in-time Shadow Copies. Select drive and the latest date that you wish to restore from.
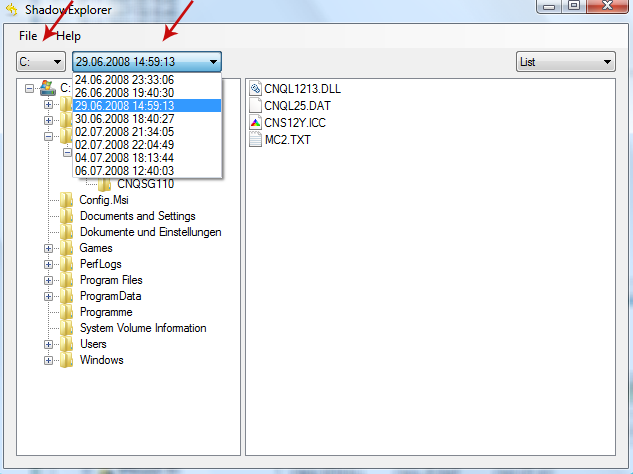
3. Righ-click any encrypted file or entire folder and Export it. You will then be prompted as to where you would like to restore the contents of the folder to.
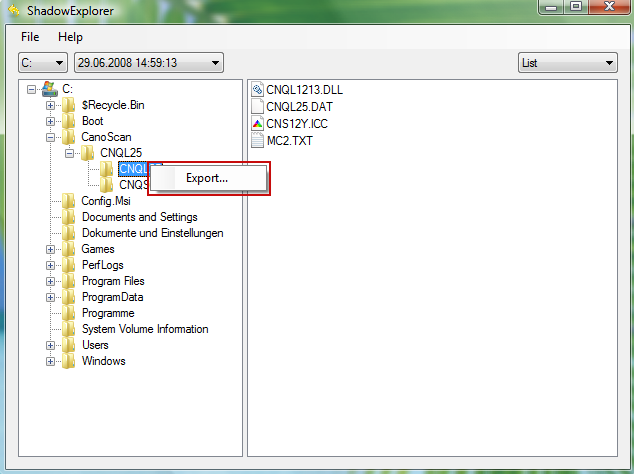
Hopefully, this will help you to restore all encrypted files or at least some of them.
Remove decoder@tutamail.com Encoder Virus and Restore Encrypted Files
4/
5
Oleh
soni agus


